Fileless worm builds cryptomining, backdoor-planting P2P botnet
A fileless worm dubbed FritzFrog has been found roping Linux-based devices – corporate servers, routers and IoT devices – with SSH servers into a P2P botnet whose apparent goal is to mine cryptocurrency.
Simultaneously, though, the malware creates a backdoor on the infected machines, allowing attackers to access it at a later date even if the SSH password has been changed in the meantime.
“When looking at the amount of code dedicated to the miner, compared with the P2P and the worm (‘cracker’) modules – we can confidently say that the attackers are much more interested in obtaining access to breached servers then making profit through Monero,” Guardicore Labs lead researcher Ophir Harpaz told Help Net Security.
“This access and control over SSH servers can be worth much more money than spreading a cryptominer. Additionally, it is possible that FritzFrog is a P2P-infrastructure-as-a-service; since it is robust enough to run any executable file or script on victim machines, this botnet can potentially be sold in the darknet and be the genie of its operators, fulfilling any of its malicious wishes.”
The worm’s targets
FritzFrog is a modular, multi-threaded and fileless SSH internet worm that attempts to grow a P2P botnet by breaking into public IP addresses, ignoring known ranges saved for private addresses.
The botnet has nodes around the globe:
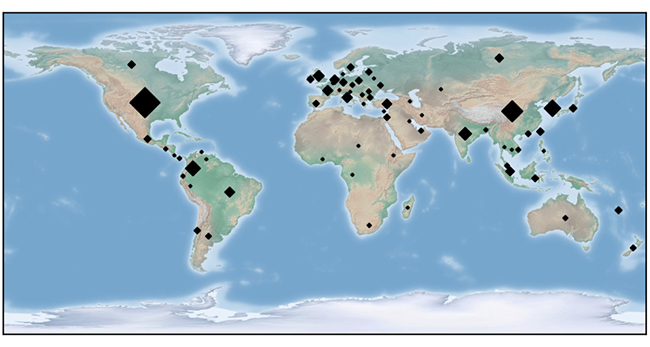
“While intercepting the FritzFrog P2P network, we’ve seen target lists which consist of sequential IP addresses, resulting in a very systematic scan of IP ranges in the internet,” Harpaz explained.
Since January 2020, it targeted IP addresses of governmental offices, educational institutions, medical centers, banks and numerous telecom companies, and successfully breached more than 500 SSH servers.
An advanced piece of malware
Written in Golang, the malware seems to be the work of highly professional software developers:
- It’s fileless – it assembles and executes payloads in-memory, operates with no working directory, and also uses the fileless approach when sharing and exchanging files between nodes
- Its brute-force attempts are aggressive, based on an extensive dictionary
- It’s efficient – no two nodes in the network attempt to “crack” the same target machine
- Its P2P protocol is proprietary and was written from scratch (i.e., not based on an existing implementation)
- It creates a backdoor in the form of an SSH-RSA public key added to the authorized_keys file. With the secret private key, the attackers can access the compromise machine whenever they want, without needing to know the SSH password
Other things that allow the malware to fly under the radar:
- It’s process runs under the names ifconfig, nginx or libexec (the latter is used when Monero-mining)
- It tunnels its P2P commands over the standard SSH port by running a local netcat client on the infected machines. Any command sent over SSH is used as netcat’s input and transmitted to the malware
“Even with this creative way of sending commands, the process remains completely automated and under the malware’s control. Even after creating this P2P channel to the newly-infected host, the malware is the one which keeps feeding the victim with commands,” Harpaz noted.
“However, it is very likely that manual, human-operated commands are sent to network peers. Guardicore Labs has developed a tool which intercepts the network and is capable of sending and receiving commands on demand. The actor behind this campaign can do the exact same thing, and it is highly probable that the operator has the means for sending commands manually to certain (or all) nodes in the network.”
Check whether your machines are part of the botnet
Detecting a cryptominer on a machine running an SSH server is not proof that it’s been infected, as the malware checks whether the machine can expend power to mine and decides against it if it can’t.
Admins can use a detection script that searches for the aforementioned fileless processes, evidence of malware listening on port 1234 and of TCP traffic over port 5555 (network traffic to the Monero pool).
While a reboot of the affected machine/device will remove the malware from memory and terminate the malware process, since a victim is immediately ‘logged’ to the P2P network along with its login credentials, it will be re-infected in no time.
Instead, admins should:
- Terminate the malicious processes
- Change the SSH password to a strong one and use public key authentication
- Remove FritzFrog’s public key from the authorized_keys file to “close” the backdoor
- Consider changing routers’ and IoT devices’ SSH port or completely disabling SSH access to them if the service is not needed