Researchers find critical RCE vulnerabilities in industrial VPN solutions
Critical vulnerabilities in several industrial VPN implementations for remotely accessing operational technology (OT) networks could allow attackers to overwrite data, execute malicious code or commands, cause a DoS condition, and more.
“Exploiting these vulnerabilities can give an attacker direct access to the field devices and cause some physical damage,” Claroty researchers noted.
The vulnerabilities
Since COVID-19 stepped on the global stage, enterprise-grade VPN installations have become a must for any organization that relies on a remote workforce. Simultaneously, they’ve become great targets for criminals looking for a way into company’s IT networks and assets.
This situation has spurred the researchers to search for vulnerabilities in industrial VPN solutions used by remote operators and third-party vendors for accessing, maintaining and monitoring field controllers, programmable logic controllers (PLCs) and input/output (IO) devices deployed at oil and gas installations, water utilities and electric utilities.
These include Secomea’s GateManager M2M Server, Moxa’s industrial VPN servers with an all-in-one secure router, and HMS Networks’s eCatcher VPN client.
Secomea’s GateManager, which is an ICS remote access server deployed worldwide as a cloud-based SaaS solution with many general-purpose and white-label instances deployed, has been found to have several flaws, all very serious:
- CVE-2020-14500 – arising from the improper handling of some of the HTTP request headers provided by the client, it could be exploited – remotely and without authentication – to execute malicious code and effectively gain access to a customer’s internal network
- CVE-2020-14508 – an off-by-one error bug that may allow an attacker to achieve RCE or cause a DoS condition
- CVE-2020-14510 – hardcoded telnet credentials
- CVE-2020-14512 – weak hash type that could reveal users’ passwords
Moxa’s EDR-G902 and EDR-G903 series secure routers/VPN servers sport a stack-based buffer overflow bug (CVE-2020-14511) that could lead to RCE.
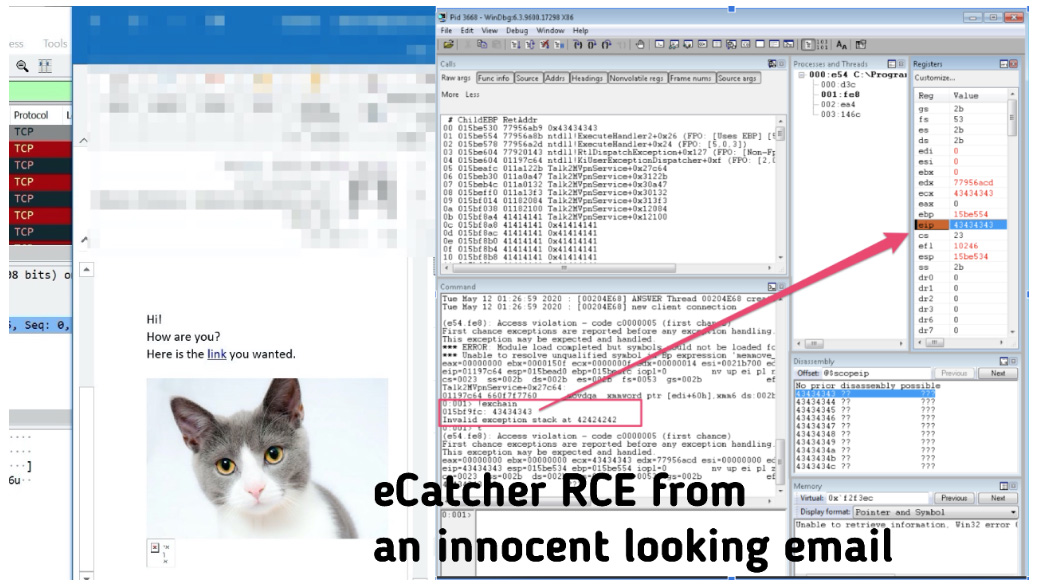
Finally, there’s a stack-buffer overflow bug (CVE-2020-14498) in HMS Networks’ eCatcher, a proprietary VPN client that is used to connect to the company’s eWon VPN device, which allows machine builders and factory owners to remotely monitor the performance of their equipment.
This bug can be triggered by tricking targets into visiting a malicious website or opening a malicious email with a specifically crafted HTML element.
“By sending socially engineered emails that embed specifically crafted images capable of exploiting CVE-2020-14498, an attacker could execute code with the highest privileges and completely take over a victim’s machine just by making the victim view the malicious email,” the researchers demonstrated.
“The exploitation phase occurs immediately when the email client (e.g. Outlook) is loading the malicious images.”
What’s next?
The good news is that all of these flaws have been patched. The bad news is there are surely more of them that have yet to be unearthed, possibly by individuals with malicious intent.
With ransomware attackers increasingly looking for ways to disrupt mission-critical systems for force companies to pay hefty sums, we can predict that, sooner or later, they will exploit vulnerabilities in OT-specific solutions.
“We would also like to emphasize that these vulnerabilities reinforce the unique risks inherent to OT remote access,” the researchers noted.
“While the security features of most VPNs make them generally well-suited and secure for IT remote access, such features tend to be less comprehensive than the stringent role- and policy-based administrative controls and monitoring capabilities required to secure OT remote access connections and minimize the risks introduced by employees and third-parties.”