H2 2019: Duration of phishing attacks grows, use of banking trojans wanes
The lifespan of phishing attacks in H2 2019 has grown considerably and resulted in the tremendous increase in the number of phishing websites blockages, says Group-IB’s Computer Emergency Response Team (CERT-GIB).
Phishers have also revised their target pool and have increasingly been targeting online services and cloud storage providers.
Diligent phishers
In H2 2019 CERT-GIB blocked a total of 8, 506 phishing web resources, while in H2 2018, the figure stood at 2,567.
This sharp upsurge in the number of blockages stems from the growing duration of phishing attacks: cybercriminals used to stop their fraudulent campaign as soon as their web pages were blocked, quickly mobilizing efforts for attacks on other brands. Today, they no longer dwell on it and continue replacing removed pages with new ones.
“Several years ago, creators of phishing pages were likely to have some technical background, they created phishing pages, putting much effort into the launch of their campaigns, preventing them from being detected and relentlessly supporting their sustainability,” CERT-GIB deputy head Yaroslav Kargalev told Help Net Security.
“This industry has changed its face — those pioneers no longer create phishing pages, they create tools for operators of web phishing campaigns who do not necessarily have any programming skills, and last year became the culmination of this trend. Since this new generation of phishers are not that experienced in maintaining the web resources viable, the phishing community’s focus has shifted toward the number of scam resources.”
Target reshuffle
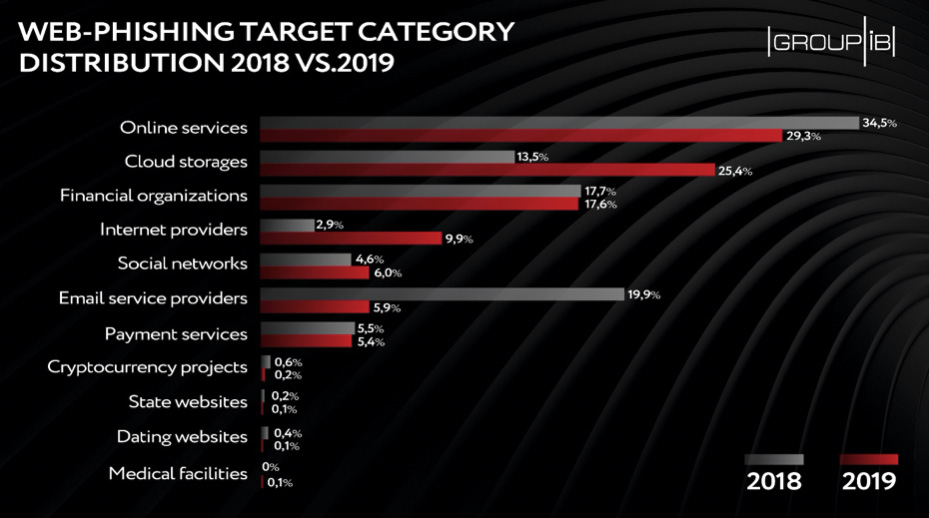
According to the figures for the past year, the Top-3 of web phishers’ targets were online services (namely client software, online streaming services, e-commerce, delivery services and etc.) (29,3%), cloud storages (25,4%), and financial organizations (17,6%).
In H2 2019, phishing attack perpetrators have revised their target pool: the number of phishing attacks on cloud storages nearly doubled, while Internet providers have seen the three-fold increase in the number of phishing scams targeting them. Both access to users’ cloud storages and accounts with internet service provider enables the attackers to get much sensitive information like personal and payment data.
This was accompanied by a lower interest to email service providers — the share of attacks on them decreased from 19,9 percent to 5,9 percent — and cryptocurrency projects, which became less attractive to cybercriminals as hype surrounding them started fading away.
Malware delivery: what’s on the menu?
In H2 2019, mail remained the main method of delivering ransomware, spyware, backdoors and other malware, used by cyber crooks in 94 percent of cases.
In the majority of cases — 98 percent — malicious items were delivered as attachments, while only 2 percent of phishing emails contained links pointing to malware. To compare, according to CERT-GIB, in H1 2019, 23 percent of phishing emails had a link in them, which might mean that malicious attachments proved to have a greater “ROI” for scammers.
To bypass corporate security systems in H2 2019, cybercriminals continued to archive their malicious attachments. About 70% of all malicious objects detected were delivered in archive files, mainly in .rar (29%) and .zip (16%) formats. Threat actors included the passwords for accessing the archives’ contents in the subject of the email, the name of the archive, or in their subsequent correspondence with the victim.
In the second half of 2019, ransomware remained the most frequent “stuffing” of phishing emails, accounting for 47 percent of the total number of malicious attachments.
Banking trojans continued losing its popularity and represented only 9 percent of malicious attachments. They, in turn, let spyware and backdoors move ahead and become the second most popular malware with a 35-percent share. The reason behind it might be the expanding functionality of backdoors, which also enables them to steal financial data and replace instruments designed for harvesting banking data only, like banking trojans.