Phishers exploit Zoom, WebEx brands to target businesses
Proofpoint researchers have spotted and documented email phishing campaigns targeting US companies in a variety of industries with emails impersonating Zoom and Cisco (Webex).

Phishing emails impersonating Zoom and WebEx
“Video conferencing has become very popular very quickly. Attackers have noticed and moved to capitalize on that popularity and brand strength,” noted Sherrod DeGrippo, Proofpoint’s Senior Director of Threat Research at Proofpoint.
“Not only are attackers using video conferencing brands as a lure for malware, but they’re using it for credential phishing, in particular to steal Zoom and Webex credentials.”
Some of the lures are not particularly original, but will surely fool some of the targets. For example, an email that welcomes users to their new Zoom account and requests them to activate their account, or an email that claims that the user has missed a scheduled Zoom conference meeting (see above).
In both cases, the attackers are after account credentials, either for Zoom or for the target’s email account.
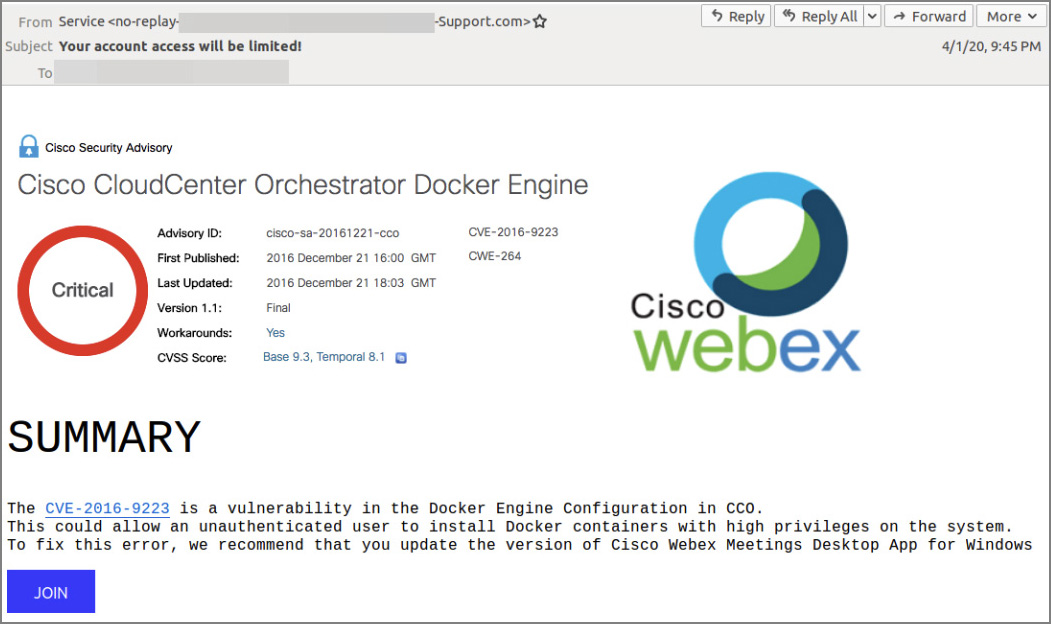
The fake emails purportedly coming from Cisco are a mishmash of unconnected visual elements and subject lines that command attention (e.g., “Critical Update!” or “Alert!”):
Many targets will spot the malicious nature of the email almost immediately, as it warns about an old vulnerability in a software that has nothing to do with Cisco Webex (apart from the fact that both are developed by Cisco.) But there’s always some recipients who panic or are inattentive enough at the moment of perusal and will end up entering their login credentials.
The value of compromised video conferencing accounts is obvious. “Stolen account credentials could be used to login to corporate video conferencing accounts and violate confidentiality. They also could likely be sold on the black market or used to gain further information about potential targets for launching additional attacks,” DeGrippo noted.
Malware delivery campaign
The researchers have also spotted an email malware delivery campaign that does not impersonate the aforementioned developers of video conferencing solutions, but does exploit their widespread use.
The emails are made to look like they are coming from a potential client who asked for a quote, says they are available for a call via Zoom, and contain a booby-trapped Excel file in the attachment, supposedly containing the sender’s schedule.
To view the contents, the recipient is asked to enable macros. If they do, the macros execute a script that, unbeknownst to the victim, installs a legitimate remote control application, which the attackers then use to access files and information on the compromised system.
Users are warned to be on the lookout for these and similar lures, and to keep in mind that phishers love nothing more than (ab)using popular brands as social engineering lures. These specific campaigns were directed at employees in US companies in the technology, accounting, aerospace, energy, healthcare, telecommunications, transportation, government, and manufacturing sectors.