What is plaguing public sector cyber readiness?
IT complexity, insider threats, and an abundance of privileged users plague public sector cyber readiness, a SolarWinds report has revealed, based on the answers from 400 IT operations and security decisionmakers, including 200 federal, 100 state and local, and 100 education respondents.
Careless and untrained insiders the leading source of security threats
For the fifth year in a row, careless and untrained insiders are the leading source of security threats for public sector organizations.
- Fifty-two percent of total respondents cited insiders as the top threat; this number is consistent for both federal and state and local respondents.
- In the education sector, respondents pointed to the general hacking community (54%) as the top threat.
Budget constraints as top obstacle
Budget constraints, followed by complexity, top the list of significant obstacles to maintaining or improving organizational IT security.
- Education respondents indicated more so than other public sector groups that budget constraints (44% in K-12) are obstacles to maintaining or improving IT security. State and local respondents indicated 27%, followed by federal respondents at 24%.
- Federal respondents indicated complexity of the internal environment (21%) is one of the most significant obstacles, surpassed only by budget constraints (24%).
- While budget constraints have declined since 2014 for the federal audience (40% in 2014; 24% in 2019), respondents also recognized the complexity of the internal environment as an obstacle that has increased (14% in 2014; 21% in 2019).
Cybersecurity maturity needs attention
Cybersecurity maturity needs attention across public sector organizations; on average, respondents rated their agency’s maturity at a 3.5 on a scale of one to five.
- Respondents indicated that their capabilities are most mature in the following areas: endpoint protection (57%), continuity of operations (57%), and identity and access management (56%). However, there was not a single cybersecurity capability for which more than 57% of respondents claimed to be organizationally mature.
Public sector lacks confidence in tackling evolving threats
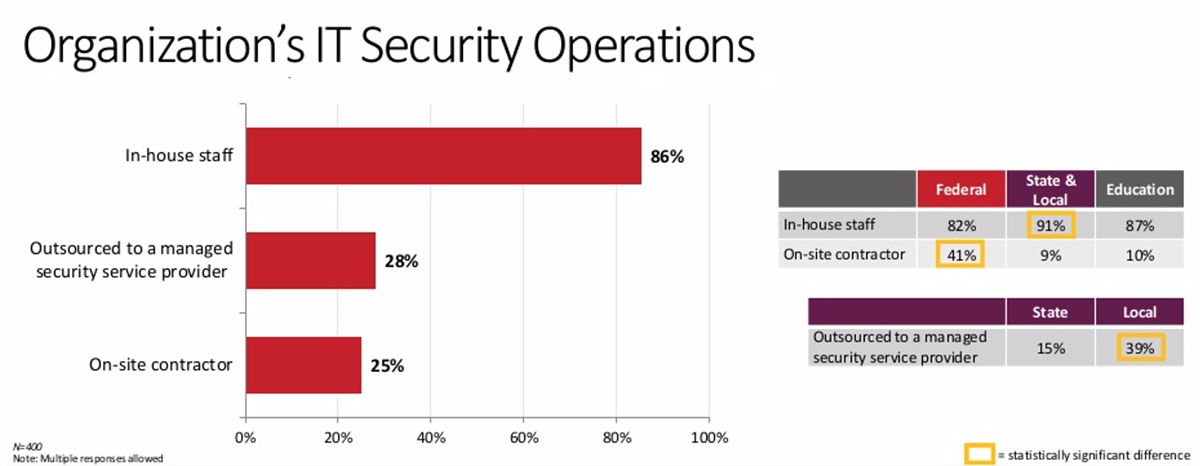
Less than half of public sector respondents are very confident in their team’s ability to keep up with evolving threats, regardless of whether the organization outsources its security operations or not.
- Forty-seven percent of respondents who outsource at least part of their security operations to a managed service provider (MSP) (28% of total respondents), feel very confident in this ability.
- The vast majority of respondents (86%) rely on in-house staff as their primary security team. Only 41% of this pool feel very confident in their team’s ability to maintain the right skills.
Evaluating metrics to measure IT security team success
Most public sector organizations measure the success of their IT security teams by evaluating metrics such as the number of detected incidents (58%) or their team’s ability to meet compliance goals (53%), which, as standalone metrics, may not accurately reflect an agency’s risk profile or the IT team’s success.
- State and local respondents were also likely to consider the number of threats that were averted (56%), while education respondents focused on level of device preparedness (46%).
- Seventy-five percent of respondents indicated compliance mandates or regulations such as GDPR, HIPAA, FISMA, RMF, DISA STIGs, etc., have had a significant or moderate impact on the evolution of their organizations’ IT security policies and practices.
Public sector orgs struggling to segment users by risk level
Public sector organizations struggle to segment users by risk level and manage the security threats posed by both privileged and non-privileged users.
- Sixty-one percent of respondents formally segment users by risk level; however, the segmentation process is challenging because of the growing number of systems users need access to (48%), the increased number of devices (45%) and the growing number of users (43%).
- Forty-one percent of respondents claimed to have privileged users not in IT. Privileged users have admin-level access to IT systems, and the extension of too much privilege across an organization can lead to increased risk.
- Nearly one-third of respondents (30%) have a formal zero-trust strategy in place; another 32% are modeling their approach based on zero trust but don’t have a formal strategy.
“These results clearly demonstrate the degree to which most public sector organizations are struggling to manage cyber risk,” said Tim Brown, vice president of security for SolarWinds.
“While it’s heartening to see that almost two-thirds of respondents are formally segmenting users—a helpful step in managing risk—the data finds careless and untrained users to still be the weakest link.
“Additionally, we’re seeing a widespread lack of organizational maturity—even in technologies like endpoint protection that have been around forever. It’s therefore no surprise that only four in ten respondents feel very confident their security team can keep up with the evolving threats.”