Healthcare industry at greatest risk of data breach
The healthcare industry has significantly more exposed attack surfaces than any other industry surveyed, according to Censys’s research findings of cloud risks and cloud maturity by industry, revealed at RSA Conference 2020.
Leveraging the Censys SaaS Platform, company researchers measured the occurrence of exposed databases and exposed remote login services – two key indicators of modern security risks – for the ten largest companies by revenue in seven major industries (Automotive, Energy, Hotels, Insurance, Manufacturing, Healthcare and Financials).
The healthcare industry showed significantly more exposed databases and more exposed remote login services.
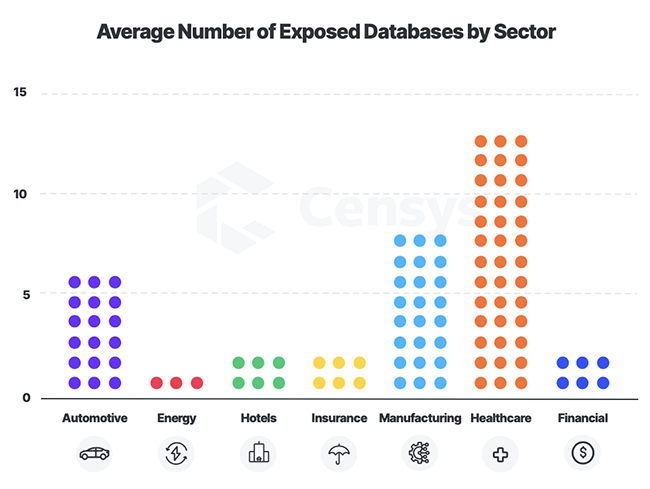
Exposed databases by industry
Composed of pharmacies, healthcare providers, insurance providers and pharmaceutical manufacturers, the healthcare industry had an average of 13 exposed databases per company. The energy industry proved the least at-risk with only one exposed database per company.
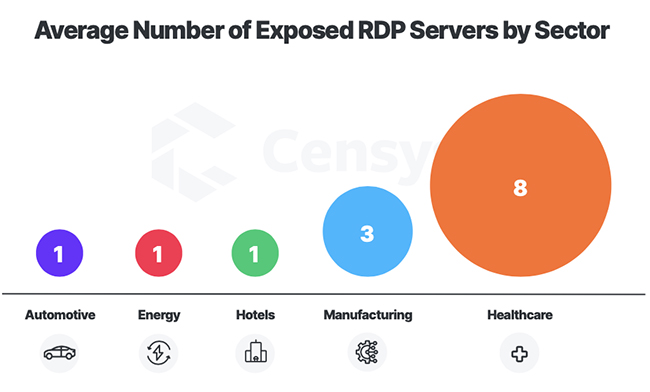
Exposed Remote Desktop Protocol (RDP)
Healthcare also had the most exposed RDP servers per company with an average of eight. However this average is caused by one outlier with ten times the number of exposed RDP servers than the next highest company.
While cloud databases and remote working solutions provide a great deal of convenience and enable modern web applications, both provide attackers a common entry point and drive data breach attacks. Internet exposed databases put customer data at risk and RDPs pose risks of credential stuffing, reuse of stolen credentials, and specific software exploits.
“Along with enormous agility for the modern enterprise, the rise of cloud infrastructure in high-tech industries has created an incredible security challenge that only continues to grow,” said Jose Nazario, Ph.D., Principal R&D Engineer at Censys. “While all industries have guilty parties, healthcare’s attack surface is simply much bigger than they realize.”
In order to protect against breaches, companies must first gain visibility using a continuous attack surface monitoring platform. This enables businesses to be alerted to risks when they occur. Companies can then remediate the issue by reconfiguring an application to listen on a private network, employing VPN software, or simply ensuring a firewall ruleset is properly configured.