Emotet can spread to poorly secured Wi-Fi networks and computers on them
Here’s yet another reason to secure Wi-Fi networks and Windows user accounts with a strong enough password: researchers have spotted and analyzed a malware program that is able to spread the Emotet Trojan to nearby wireless networks and compromise computers on them.
Emotet: An old threat
Emotet is one of the most versatile malware threats out there.
Its ability to download additional malware (more often than not the Trickbot Trojan – another huge enterprise threat) is just one of the things it’s capable of due to its modular nature.
Until now, Emotet was known to be able to deliver itself to other computers on the same network thanks to its propagation component, which spreads the malware via mounted shares or the use of exploits.
But, according to Binary Defense researchers, it now has another, even more dangerous propagation trick that allows it to “hop” onto other Wi-Fi networks and try to compromise computers on it.
A new spreading capability
“We retrieved this malware sample from an Emotet bot used for research and reverse-engineered the malware code using IDA Pro to determine how it operates,” Randy Pargman, senior director of threat hunting and counterintelligence at Binary Defense, told Help Net Security.
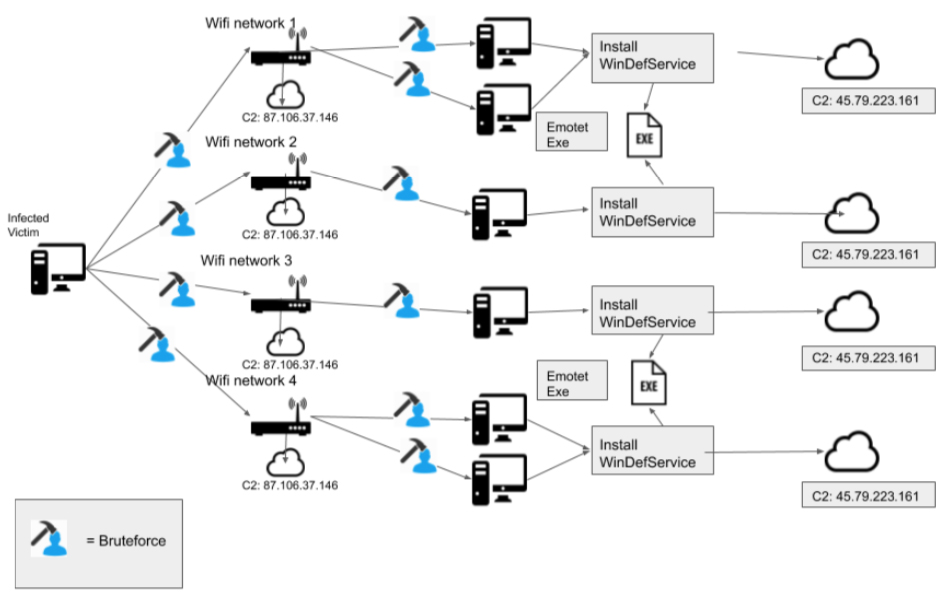
After the malware infects a computer that has Wi-Fi capability, it uses the wlanAPI interface to discover any Wi-Fi networks in the area: a neighbor’s Wi-Fi network, a free Wi-Fi network at a café, or a Wi-Fi network of a nearby business.
“Even if those networks are protected with a password required to join, the malware tries a list of possible passwords and if one of the guessed passwords works to connect to the Wi-Fi network, it will join the infected computer to that network,” Pargman explained.
“Once it is on the network, the malware scans all other computers connected to the same network for any Windows computers that have file sharing enabled. It then retrieves the list of all user accounts on those computers and attempts to guess the passwords to those accounts as well as the Administrator account. If any of the guessed passwords are correct, the malware copies itself to that computer and installs itself by running a remote command on the other computer.”
Lastly, is reports back to the command and control server to confirm the installation.
Some interesting details
One interesting thing discovered during the analysis is that the main executable file the malware uses for wireless spreading has a timestamp that dates back to April 2018 and was first submitted to VirusTotal a month later.
“The executable with this timestamp contained a hard-coded IP address of a Command and Control (C2) server that was used by Emotet. This hints that this Wi-Fi spreading behavior has been running unnoticed for close to two years,” noted James Quinn, a threat researcher at Binary Defense.
“This may be in part due to how infrequently the binary is dropped. Based on our records, 01/23/2020 was the first time that Binary Defense observed this file being delivered by Emotet, despite having data going back to when Emotet first came back in late August of 2019.”
Another thing that might explain the low profile of this malware is that its exploitation of the wlanAPI for network profiling will not be triggered if researchers run it in VMs/automated sandboxes with no Wi-Fi adapter.