CrackQ: Efficient password cracking for pentesters and red teamers
CrackQ employs automation to make password cracking a faster and more efficient undertaking for pentesters and red teamers.
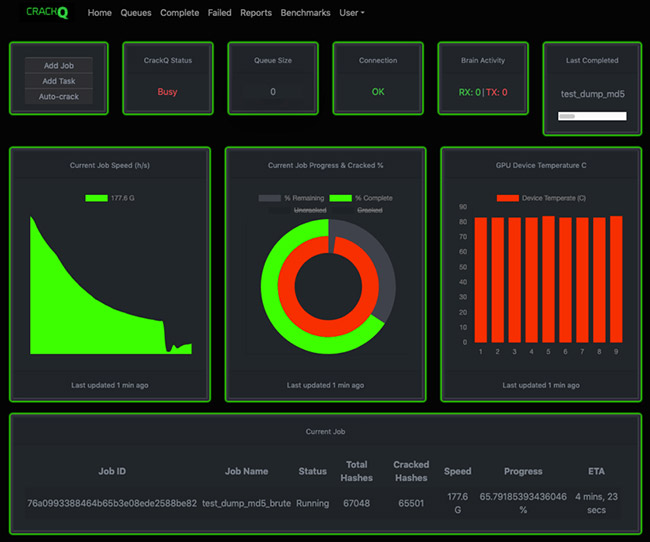
CrackQ dashboard
“Regular security testing is a practice all organizations should incorporate into their overall security programs. Password cracking is an essential phase of a pentest/red team engagement and helps asses organizational security best practices,” Dan Turner, Principal Security Consultant at Trustwave SpiderLabs and author of CrackQ, told Help Net Security.
“But pentests and red teaming engagements have strict time constraints – whereas threat actors have unlimited time for targeting and tool calibration. Security professionals are at a testing disadvantage, and need advanced automation tools of their own.”
Password cracking for pentesters
CrackQ is an interface for the open source password recovery/cracking tool Hashcat. It is served by a REST API and a JavaScript front-end web application for ease of use.
“It is primarily a queuing system to manage password cracking for offensive security teams during red teaming and pentesting engagements,” Turner explained.
CrackQ supports SAML2 and LDAP authentication with MFA, uses a newly created analysis library (Pypal) and generates password analysis reports from the results of specific password cracking jobs (shows insecure password choices and patterns within an organization).
It is able to perform automated re-queuing on job failure, provides multi-user support, and it will use the Hashcat brain automatically when it’s effective to do so (i.e., when slow-speed algorithms are in play).

Add job window with hash type search functionality

Generate a report for a job from the complete queue
Plans for future development
The tool is currently in alpha and Turner hopes a community of developers will spring up and help develop it further.
Future releases will include additional automation, efficiency improvements, and more advanced cracking techniques, he told us.
It will include an autocrack option that automatically chooses efficient cracking techniques based on the type of password, hash algorithm and a chosen time period, as well as:
- Additional techniques: PACK, Prince, Omen, PCFG
- Automated queue manipulation for better efficiency
- Automated background cracking of leak dumps with lower priority queues
- Custom wordlist creation using a web/social media crawler.