Product showcase: Alsid for AD
You are using Active Directory (AD) every day, every hour, every minute when you log into your device, open your emails, access an application, or share a file.
But, guess what, it’s also used by hackers on a daily basis. Simply put, when attackers take control of your AD, they inherit godlike powers over your IT. Sweet.
Analyzing attack vectors: How attack pathways are born
Active Directory itself is a robust product that suffered few zero-day vulnerabilities in its history. However, Active Directory implementations inevitably become weak. Every change in business architecture, each M&A operation, every server that you add will alter your AD topology. Give it a year, and any AD will grow into a beast you can’t comprehend anymore.
Past that point, it becomes impossible to understand the possible ripple effects of the changes made to your AD. Some have a significant impact on your security posture, and you just won’t know about it.
AD security tactics that don’t work
First: SIEM-based monitoring. Identifying AD risks with SIEMs inescapably requires writing dedicated rules, which often generate an overwhelming flood of false positives. Not even mentioning that the most effective attacks, such as DCShadow, simply don’t leave any logs behind.
Now: basic hygiene. Admittedly mandatory to any effective defense, maintaining proper hygiene for AD is a challenge, to say the least. Every simple task requires a custom script to run constantly. Chain all checks together, and you’ll have a system that just doesn’t work IRL.
Finally, the handful of dedicated AD solutions that automate correlation and hygiene processes all require locally-installed agents and elevated rights, which makes them impractical for any sensible AD admin.
Alsid for AD: A new approach to Active Directory security
Our approach is security focused, targeting attacks patterns and providing AD-specific insights and controls for hardening your Active Directory, detecting breaches in real time, and accelerating AD forensic investigations.
From a user experience standpoint, Alsid for AD is agent-less, makes zero change to the Domain Controller and requires no privilege at all.
Setting up Alsid for AD
Alsid for AD is being hosted on a dedicated cloud environment, provided and managed by Alsid. Our platform connects to our users’ AD through an encrypted VPN.
Once connected, Alsid for AD starts calculating your infrastructure’s exposure. Insights and hardening recommendations are provided after a few minutes of initial computation.

Simple architecture design

Alsid relies on standard protocols only
All sensible defense strategies start by reducing threat exposure. Dwarfing the adversary’s ability to exploit openings is a critical step… that’s easier said than done for Active Directory, considering its size and complexity.
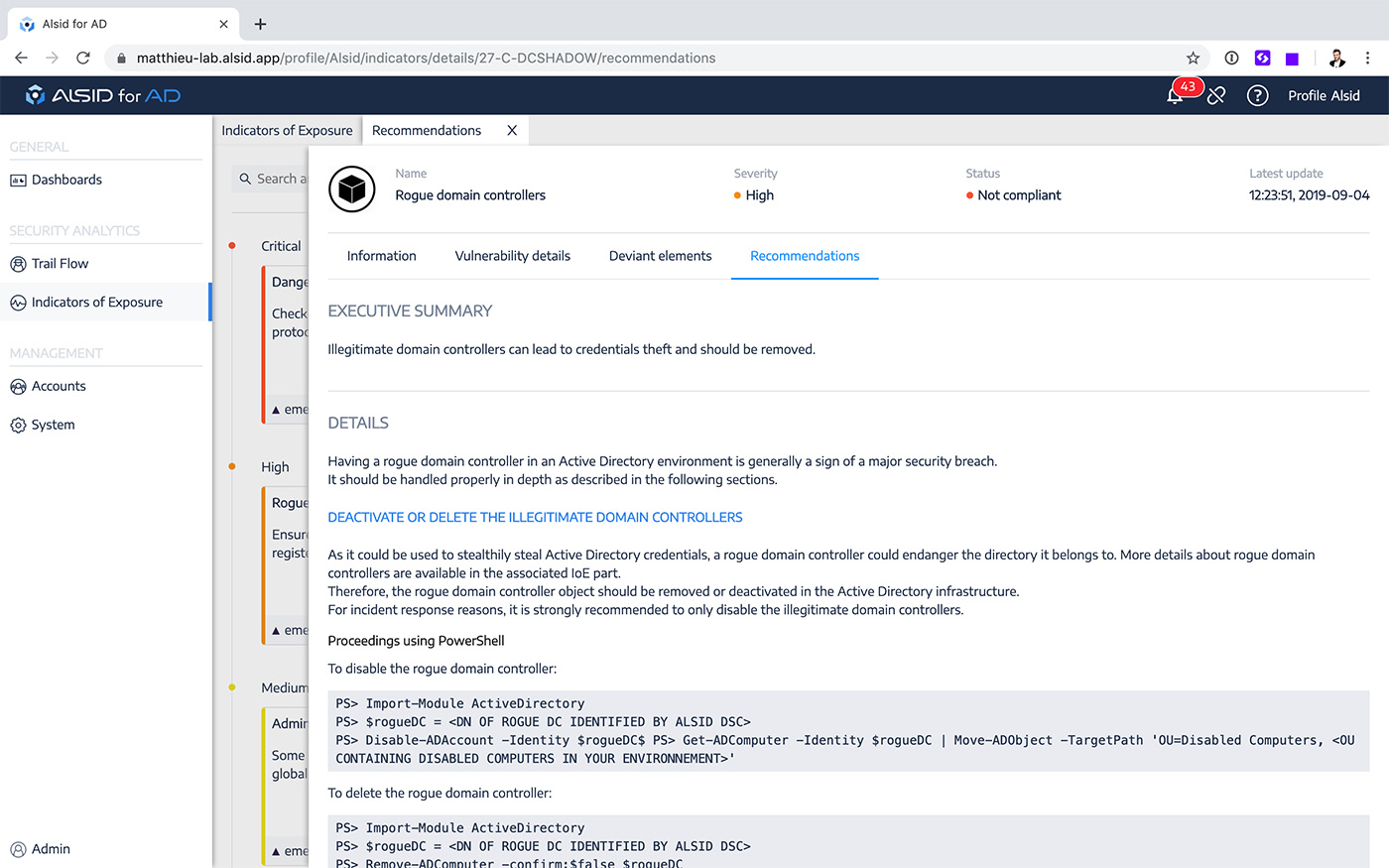
Alsid for AD constantly scans your AD to find existing misconfigurations and weaknesses. Those Indicators of Exposure (IoE) provide descriptions, threat scores, estimations of remediation costs, and step-by-step mitigation plans. A comprehensive list of IoE is provided here.
Live indicators of exposure
Detailed remediation plans
Most solutions available today are either impractical or, at best, detect attacks after they’ve succeeded, which effectively defeats the purpose of any sensible defense.
Alsid for AD capabilities
Alsid for AD combines 3 unique characteristics:
- True real-time monitoring – Our AD-native platform does not rely on Windows logs and provides insights in true real-time. Considering the vast amount of damage a rogue admin can do in only a few minutes, real-time is not an option… but remains unseen in other solutions.
- AD-native intelligence – Alsid maintains an always up-to-date intelligence database of attack patterns. Our research team constantly enriches our platform’s detection engine accordingly, making it market’s gold standard when it comes to attack coverage.
- Before-compromise detection – AD-targeted attacks are chains of several events that, together, eventually lead to a breach. Alsid for AD, very uniquely, detects each of these events independently, so our platform will alert its users before the eventual breach happens. So, our users can remediate to attacks before they succeed.
Real-time detection and alerting
Responding to breaches: How to investigate and hunt
After a breach, incident responders investigate the attack to inform remediation. For AD, most practitioners use Microsoft Event logs, an extremely inefficient task considering the huge volume of (mostly irrelevant) data they find there.
Alsid for AD keeps a complete history of all security-meaningful events. Using our advanced query system, investigators drill down into these events with a speed and accuracy only a true AD-native technology permits.
Furthermore, Alsid for AD integrates seamlessly with orchestrators, so users can remediate to breaches at machine speed.
AD-native investigation capabilities
Conclusion
AD-related attacks are now common-place. Reports show repeatedly that AD admin and security folks struggle to deal with AD-related threat.
This is our battlefield. Don’t take our word for it: give Alsid a test-run and start improving your infrastructure’s resilience.