Should you block newly registered domains? Researchers say yes
7 out of 10 newly registered domains (NRDs) are either malicious, suspicious or not safe for work, say Palo Alto Networks researchers, and advise organizations to block access to them with URL filtering.

“While this may be deemed a bit aggressive by some due to potential false-positives, the risk from threats via NRDs is much greater. At the bare minimum, if access to NRDs are allowed, then alerts should be set up for additional visibility,” they noted.
What is an NRD?
The researchers consider a domain to be “newly registered” if it’s been registered or had a change in ownership within the last 32 days.
Newly registered domains can, of course, be benign, but the fact that over 70 percent of them are malicious or otherwise potentially harmful to organizations and their members should definitely spur admins to consider blocking access to them at the network level.
Here’s another reason for this move: most NRDs used for malicious purposes are “alive” for a very short while – a few hours or days – and security vendors might not spot them and react in time to block them.
Other interesting facts
Malicious or potentially harmful NRDs are set up to serve as C&C channels; distribute malware, potentially unwanted programs and adware; host phishing pages and scam pages; send email spam. “Not safe for work” domains host content that might be objectionable in an enterprise setting (adult content, gambling, etc.).
Threat actors use various techniques for their malicious domains to fly under the radar of automatic detection tools. For example, a phishing domain might be using a CAPTCHA so that crawlers don’t access the actual phishing page.
The creation of malicious NRDs can be automated. Domains that serve as a C&C channel or for data exfiltration are often generated/registered on demand, by using domain generation algorithms. Phishing pages, on the other hand, are often set up on typosquatted domains (e.g., mocrosoft.cf) and the phishers are counting on users tendency to mistype actual (popular) URLs they want to visit.
Palo Alto Networks says that their system identifies, on average, about 200,000 NRDs every day.
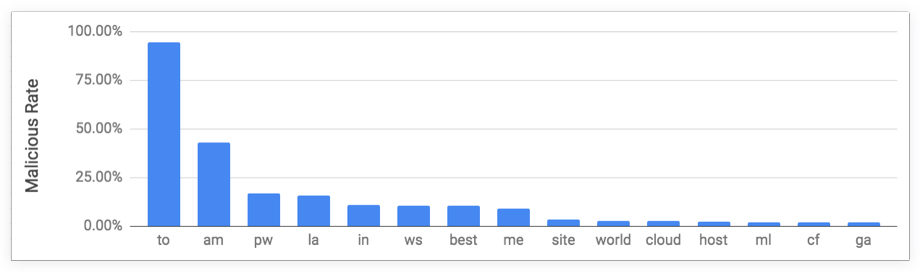
While malicious NRDs ending in .com, .tk, .cn and .uk are the most numerous, country code top-level domains for Tonga, Armenia and the Republic of Palau have the highest malicious NRD rate:
“We would even go as far as to recommend blocking complete TLDs that are mainly utilized by bad actors. Of course, each organization must understand what their tolerance is for potential false-positives when blocking whole TLDs,” the researchers pointed out.
UPDATE (September 5, 2019, 2:00 a.m. PT):
Palo Alto Networks’ researchers revised the list of the top 15 TLDs with the highest malicious NRD rate, as some of the somains were just contacted by malware but not actually registered. We have revised the article to include the revised chart.