Despite disclosure laws, cybercrime may be widely underreported
While attack vectors remain largely the same year over year, attack volume will increase and cybercrime may be vastly underreported, according to the 2019 State of Cybersecurity Study from global IT and cybersecurity association ISACA.
“Underreporting cybercrime – even when disclosure is legally mandated – appears to be the norm, which is a significant concern,” said Greg Touhill, Brigadier General (ret), ISACA Board Director, president of Cyxtera Federal and the first US Federal CISO. “Half of all survey respondents believe most enterprises underreport cybercrime, even when it is required to do so.”
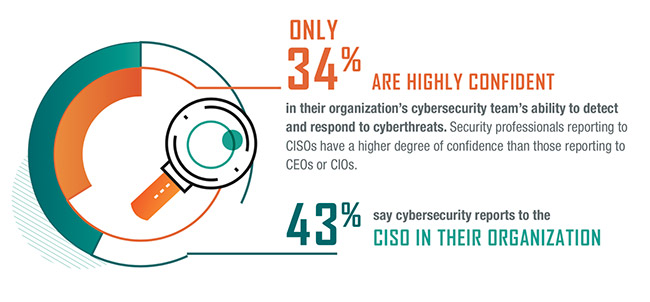
Equally concerning, only 1 in 3 cybersecurity leaders (34 percent) have high levels of confidence in their cybersecurity team’s ability to detect and respond to cyberthreats. The highest levels of confidence are correlated with teams that report directly into the CISO, and the lowest levels are correlated with teams reporting into the CIO. According to the study, 43 percent of respondents say their teams report to a CISO, and 27 percent report to a CIO.
“What we can conclude from this year’s study is that governance dictates confidence level in cybersecurity,” said Frank Downs, director of ISACA’s cybersecurity practices. “When the cybersecurity team reports directly to a designated and experienced cybersecurity executive, cybersecurity teams report having significantly more confidence in their team’s capability to detect attacks and respond effectively.”
These findings indicate the confusion enterprises experience when structuring cybersecurity with information technology. A CIO’s main goal is managing and implementing information technology, which is substantially different than securing and protecting it. In this reporting structure, cybersecurity can fall to a secondary consideration, leading to a team’s lack of confidence to be cyber ready. In fact, a higher percentage of respondents are confident in cybersecurity reporting to the CEO than to the CIO.
ISACA’s State of Cybersecurity Study captures the perspectives of more than 1,500 individuals who define the field—cybersecurity managers and practitioners from across the globe. Part 1, released in March, highlighted workforce trends and challenges. Part 2, released today at Infosecurity Europe, covers attack trends.
According to State of Cybersecurity Part 2, the top three threat actors remain cybercriminals, hackers and non-malicious insiders. Phishing, malware and social engineering top the list of prevalent attack types for the third year in a row. Ransomware is significantly down from 2018, with 37 percent of organizations reporting that they experienced ransomware in last year’s study, compared to 20 percent this year.
Just under half of organizations report an increase in cybersecurity attacks on their organization this year, and 79 percent say it is likely they will experience a cyberattack next year.

“The cyber landscape is complex. Cybersecurity, though in focus today, suffers from a siloed and static approach,” said Renju Varghese, Fellow & Chief Architect, CyberSecurity & GRC, at HCL Technologies. “Many teams are missing the attacks that significantly impact organizations because they don’t have the size or expertise to keep up with the attackers and are overwhelmed. Moreover, their existing security tools and processes are segregated and seldom work in tandem, leaving the teams staring at multiple consoles and drowning in alerts and incidents.”
However, by carefully analyzing the variables that contribute to incident susceptibility and team inefficiency, organizations can better prepare themselves for the dangers presented by cyber miscreants, says ISACA’s Downs. Specifically, analyzing key organizational attributes identified in the State of Cybersecurity, such as cyber reporting structure, prevalent attack methods and team readiness through a culture of continuing professional education, organizations can increase their resilience to potential incidents.