GitHub introduces Dependabot-powered automated security fixes
GitHub, the largest code-hosting site in the world, has announced many new features and changes at the 2019 GitHub Satellite conference that took place last week in Berlin.
The feature that drew the most attention is GitHub Sponsors, which will allow users to financially support developers and maintainers of software they use every day. Microsoft – GitHub’s owner since October 2018 – has waived platform fees for sponsors, has pledged to cover payment processing fees for the first 12 months of the program and to match all contributions up to $5,000 during a developer’s first year in GitHub Sponsors.
But GitHub has also announced new and improved security tools for open source developers.
Improved tools
- The coverage of the security alerts feature, introduced in 2017 to warn developers about vulnerabilities in software packages which their projects depend on, has been broadened and deepened with data from open source security company WhiteSource
- GitHub’s token scanning has been broadened to include scanning for tokens issued by Alibaba Cloud, Mailgun, and Twilio
- Dependency insights – enterprises can use it to quickly audit dependencies and better understand their exposure when a security vulnerability is released publicly.
A private workspace to discuss, fix, and publish security advisories
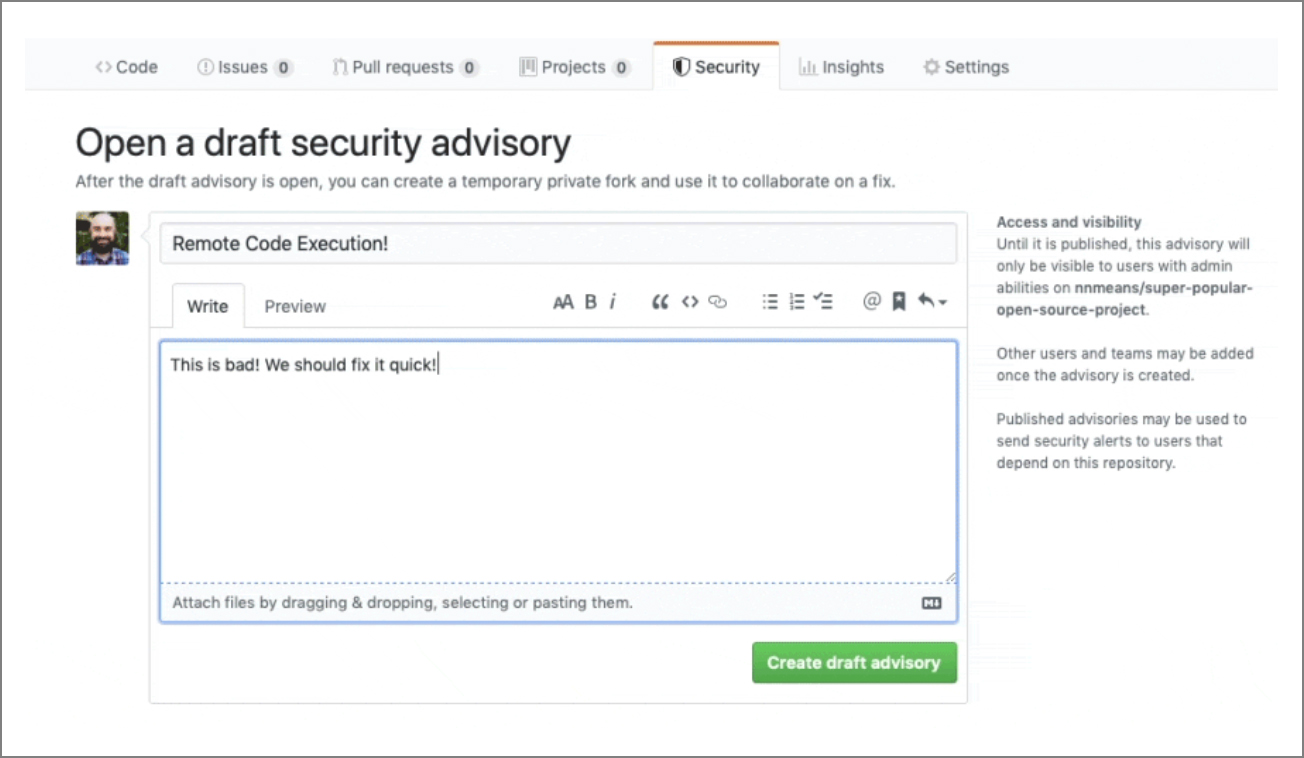
A new feature that has been enthusiastically welcomed is maintainer security advisories, which allow them to create a draft advisory, use it to privately discuss the impact of a vulnerability on their project and collaborate to fix the flaw.
One thing that seems to have gotten hidden from the GitHub announcements is actually THE MOST VALUABLE feature for open source maintainers:
The ability to have private discussions and code review about security vulnerabilities WITHIN your repo. https://t.co/voCvmla3s0 pic.twitter.com/dGMDP28r3T
— jessie frazelle 👩🏼🚀 (@jessfraz) May 23, 2019
The feature is still in beta and, for the moment, only administrator users can create the advisories. Ultimately, though, the goal is to allow non-administrator users to report issues by creating advisories.
Also, we shipped support for keeping a repo security policy, which should help answer the question of, ‘How should I report this security issue?’ for non-admin reporters,” noted GitHub engineer Steve Richert.
Automated security fixes with Dependabot
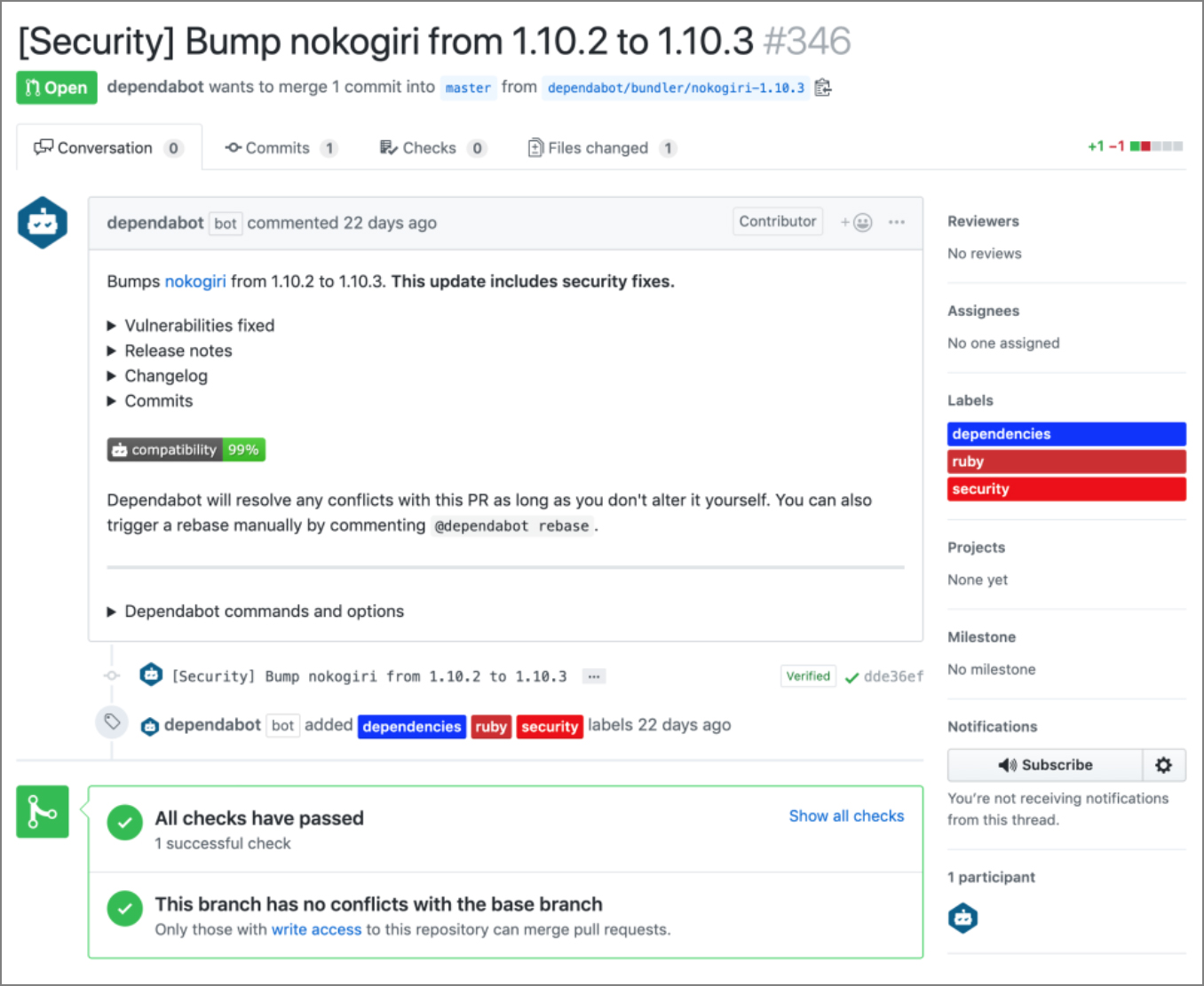
Finally, GitHub has announced the acquisition and integration of Dependabot.
“With the help of Dependabot, GitHub will monitor your dependencies for known security vulnerabilities and automatically open pull requests to update them to the minimum required version,” Justin Hutchings, Senior Product Manager at GitHub, explained, and said that the company will be rolling out automated pull requests to all accounts with security alerts enabled over the coming months.
“Automated security fixes are opened by Dependabot on behalf of GitHub. The Dependabot GitHub App is automatically installed on every repository where automated security fixes are enabled,” the company noted.
Automated security requests contain information about the vulnerability, such as release notes, changelog entries, and commit details, but also compatibility scores, which show developers how likely it is for the security update to cause breaking changes to their project.