Microsoft adds tamper protection to Microsoft Defender ATP
Microsoft has added a new tamper protection feature to Microsoft Defender ATP (formerly Windows Defender ATP) antimalware solution.
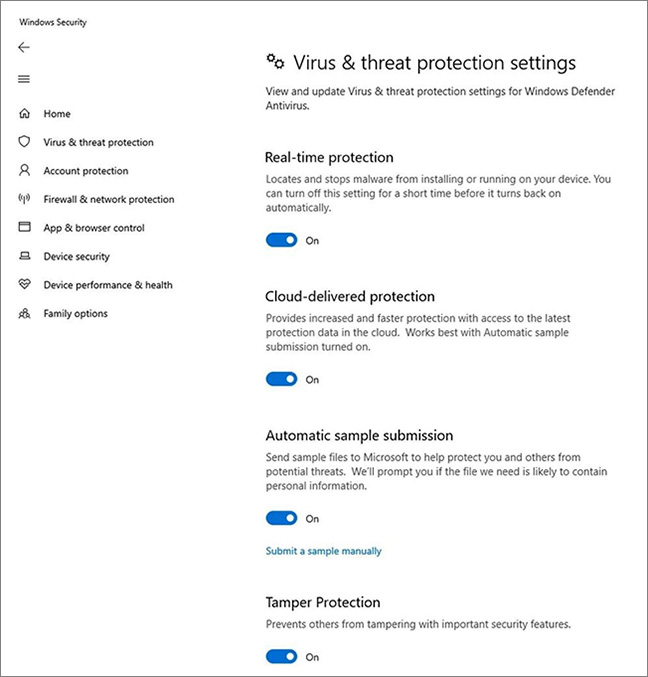
When turned on, it should prevent malicious apps and actors from disabling the antimalware solution or some of its key security features.
Foiling often-used tactics
Malware developers are forever looking for ways to make its wares “invisible” to users, AV/antimalware software and malware analysts.
They pursue the first goal by disguising the malware as a legitime document or app and minimizing the noticeable effects it may have on the target system, and the last one by making the malware capable of detecting (virtual) malware analysis environments and terminating/altering its behavior if it does.
They attempt to hide the malware from AV software by using a wide variety of tactics, including dropping additional malware/scamware to pass unnoticed or disabling AV software altogether. The latter effect can be achieved through a variety of approaches, such as dropping AV software’s certificates in the “untrusted certificates” list, terminating them and deleting their files, and so on.
The new feature
The new tamper protection feature will prevent attackers from disabling:
- Real-time protection
- Cloud-delivered protection (that neutralizes previously unknown malware)
- The IOfficeAntivirus detection feature (a mechanism to scan a file before opening or sending via email)
- Behavior monitoring (for spotting and blocking suspicious processes)
- The implementation of security intelligence updates.
It should also prevent them from disabling of the entire antimalware solution.
Home users will be able to switch it off (through the Windows Security app).
“For Windows home users, the feature will be On by default when Windows is installed. If you are upgrading and Cloud-delivered protection is enabled, then the tampering protection feature will also be turned On,” Microsoft explained.
“For enterprise customers (such as those with a Microsoft Defender ATP license), this feature will be opt-in and can only be managed from the Intune management console. Local device admin users will not be able to change the setting. This ensures that even malicious apps – or malicious actors – can’t locally override the setting.”
The feature is currently being tested, and is available only to Windows Insiders.
“The full functionality of the feature (including support for enterprise-level management) will be released along with the upcoming release of Windows 10,” Microsoft announced.