Researchers expose massive mobile adware and data stealing campaigns with 250 million downloads
Check Point Research has uncovered two massive mobile adware and data stealing campaigns, which have already had over 250 million downloads combined globally. Both target mobiles using Android, and exploit the mobile app development supply chain to infect devices and perform malicious actions.
SimBad’s malicious ads
SimBad is a massive mobile adware campaign that has already had 147 million downloads across 210 infected apps on the Google Play Store. Called SimBad because most of the infected apps are simulator games, the worldwide campaign makes phone usage unbearable to users by displaying countless ads outside of the app, with no visible way to uninstall the incriminating apps. The apps’ malicious behavior includes:
1. Showing ads outside of the application, for example when the user unlocks their phone or uses other apps.
2. Constantly opening Google Play or 9Apps Store and redirecting to another particular application, so the developer can profit from additional installations.
3. Hiding its icon to prevent uninstallation.
4. Opening a web browser with links provided by the app developer, enabling targeted spear-phishing on users
5. Downloading APK files and asking the user to install it, or stealthily downloading malware
6. Searching a word provided by the app in Google Play.

SimBad attack flow
SimBad can also generate phishing pages for multiple platforms and open them in a browser, thus performing spear-phishing attacks on the user. Google was notified about the apps and quickly removed them from the Google Play Store.
Operation Sheep shaves users’ personal details
Check Point Research also discovered a group of Android applications massively harvesting contact information on mobile phones without the user’s consent. The 12 different apps all use a data-scraping Software Development Kit (SDK) and have so far been downloaded 111 million times. Dubbed ‘Operation Sheep’, this massive data stealing campaign is the first known campaign seen in the wild to exploit the Man-in-the-Disk vulnerability revealed by Check Point Research in 2018.
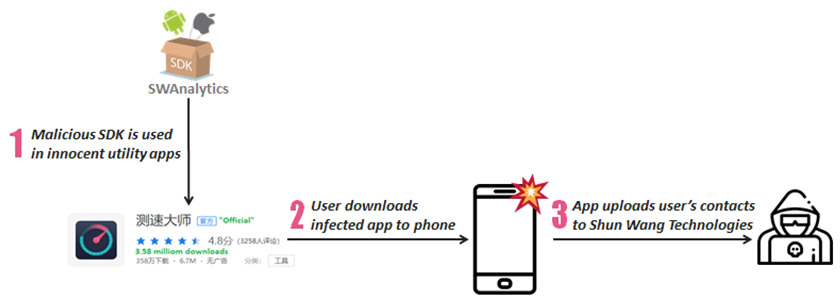
Operation Sheep attack flow
The SDK, named SWAnalytics, is integrated into seemingly innocent Android applications published on major 3rd party Chinese app stores such as Tencent MyApp, Wandoujia, Huawei App Store, and Xiaomi App Store. After app installation, whenever SWAnalytics senses victims opening up infected applications or rebooting their phones, it silently uploads their entire contacts list to Hangzhou Shun Wang Technologies controlled servers. In theory, this means the attacker could have collected the names and contact numbers of one-third of China’s entire population.
Such data could, of course, circulate in underground markets for further exploit, ranging from rogue marketing, targeted telephone scams or friend referral program abuse. Interestingly, the exploit seems to ignore old Android devices below Marshmallow deliberately (Marshmallow and above is used on 70% of Android devices). This is believed to be a time- and money-saving tradeoff to prolong compatibility and keep the malicious code simple. Also, the exploit does not collect data at all from Meitu Phone devices.
About supply chain attacks
Modern software applications, such as websites or mobile phone apps, are built using complex supply chains of third-party libraries or open source components. These off-the-shelf solutions help an organization’s software engineers to accelerate app development. However, third-party code is prone to supply chain attacks, in which attackers leverage trusted third party vendors to deliver malware to unsuspecting customers by inserting malware into third-party code. From the attacker’s point of view, poisoning a company’s software supply chain by infecting one of the components within it is highly tempting and arguably easier than a direct attack on the organization itself.
Organizations tend to trust that the third party code they use has built-in security. Unfortunately this is not always the case. As third-party providers often prioritize speed to market over security, it means their code can easily be intercepted and compromised. Attackers also know that DevOps teams often develop and deploy applications without the necessary security checks. Knowing this allows them to take advantage of these sacrifices of security concerns.
Furthermore, there is no good way to partition third party libraries or code from organization’s in-house code: it all runs within the same privilege. That means that anything the application can do, all the libraries can also do. So if the application can access your database, there is nothing to stop your libraries from doing the same.
Unfortunately, there is no easy answer for defending against these types of attacks. Organizations need to understand what commercial and open source products they are using, and be aware of and prepared for potential attacks using legitimate software as a vector.