Most popular home routers lack basic software security features
It’s no secret that too many Internet of Things devices lack adequate security. But is it too much to expect that out home routers – the devices that “provide” us with a working Internet connection – implement the most basic software security hardening features?
Apparently, it is, even though some of them are easy to adopt, have no downsides, and are standard practices in the desktop and mobile software markets.
The analysis
Parker Thompson and Sarah Zatko, two researchers with the Cyber Independent Testing Lab (Cyber-ITL), have searched the firmware image of 28 Linux-based home router models for basic security features that come with the Linux operating system:
- Address Space Layout Randomization (ASLR)
- Non-executable stack segments (Data Execution Prevention – DEP)
- Correct ordering and marking of segments in the binary to prevent overwriting jump-tables for Linux systems (RELocation Read-Only – RELRO)
- Stack canaries to thwart stack overwrites (Stack Guards).
The researchers analyzed each binary in the firmware images of 10 MIPS-based and 18 ARM-based devices: popular home routers by Asus, D-LINK, Linksys, Netgear, Synology, TP-Link and Trendnet that were listed in the 2018 Consumer Reports home router buying guide and “Best of 2018” home router lists by several online tech/consumer electronic outlets.
The depressing results
They have compiled two tables that show the results (the first line of both tables references the basic desktop distribution of an un-hardened Linux Ubuntu Long Term Support, dating back to 2016, for comparison):


The results of their analysis showed many things:
- All of the tested devices – whether MIPS- or ARM-based – are lacking basic application armoring features provided by the underlying operating system
- An old bug in the Linux/MIPS stack that made the implementation of DEP protection impossible in MIPS-based devices
- While none of the reviewed routers scored well, the Linksys wrt32x scored the best (even though it’s ASLR protection is essentially non-existent).
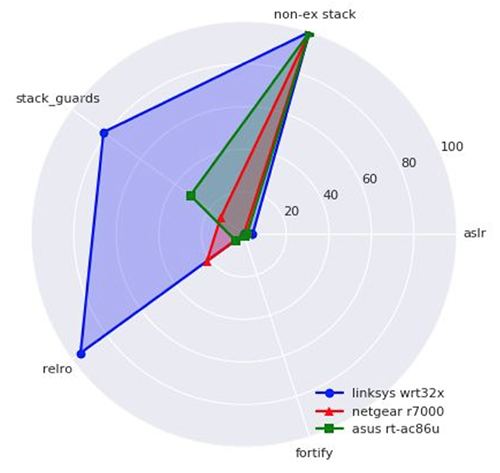
The researchers also found that the use of safety features is not consistent across different models within the same brand name.
“If vendors applied basic checks for software safety practices as part of their build and testing practices prior to shipping their products the industry could quickly see a noticeable improvement in product build safety,” the researchers pointed out.
“For vendors, this state of affairs presents an opportunity for any brand wishing to distinguish itself: very little effort is currently required to earn a ‘best in class’ designation.”