Retail and finance top the list of vulnerable industries, increasingly targeted with credential threat campaigns
The finance, professional, and information sectors had the highest volume and most variety of malicious activity in Q2 2018, says Rapid7, and the manufacturing sector is steadily getting more and more targeted.

According to the statistics from the company’s latest threat report, compiled from alerts validated by its Managed Detection and Response team and data from its Project Sonar (Internet scanning for vulnerable systems) and Project Heisenberg (150+ honeypot nodes watching for signs of attacker activity), there has also been a continued emphasis on credential theft and account leaks across all industries, along with an increase in remote access attempts.
Half of the threat activity targeting small organizations was remote entry
“While remote entry also made up a significant amount of the activity targeting large organizations, the top incident type we saw facing large organizations in Q2 was dangerous user behavior,” the researchers shared.
“We also observed that dangerous user behavior is directly tied to the potential for attackers to attempt more remote entry attacks against these organizations moving forward, as users visit URLs designed to steal credentials. The majority of credential theft URLs were directed against large organizations.”
Brute-force attacks against local accounts suddenly topped the list of top threat events in June
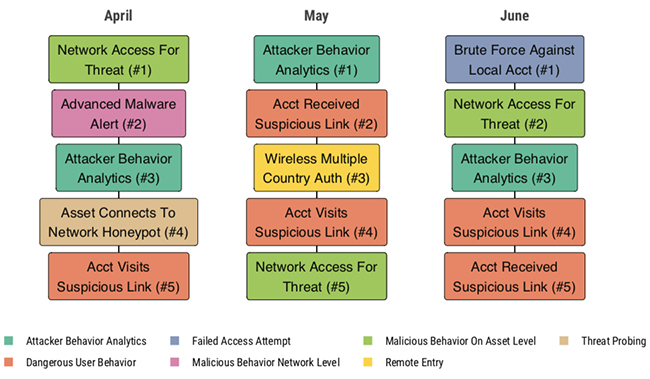
This jump was fueled by adversaries’ consistent interest in Microsoft’s Remote Desktop Protocol (RDP) and a steady increase in activity targeting Microsoft’s Server Message Block (SMB) protocol.
“Although there are exploits available for RDP, many attackers prefer to leverage credentials to gain access to systems over RDP,” the researchers noted.
Among these is the SamSam attacker (or group), who stole millions from US companies by deploying ransomware on many target computers on the corporate network simultaneously.
The attackers are trying out usernames with no passwords, common and uncommon (but very specific passwords), and are tageting backups and other systems that are easy for defenders to overlook but can serve as a way into the network.
The rise of the cryptominer injectors
In Q2 2018 we witnessed the cryptojacking campaign that relied on compromised MikroTik routers, which served users with pages injected with the Coinhive mining script.
Web servers running Drupal were also under attack, and one of the goals was to install cryptominers on them.
“Q2 saw increased attacker focus on Bitcoin, numerous flavors of HTTP attacks, the start of an uptick in Mirai and a levelling-off of SMB,” the researchers noted.
They advised those who run a bitcoin node to make sure the software is from a trusted source and at current patch levels; users to rethink how they configure, manage and, expose their cameras, doorbells, and security systems; and organizations to ensure they have the level of DoS protection that meets their risk appetite.