Access to airport’s security system sold on dark web
Leveraging compromised RDP credentials is one of the easiest ways attackers can break into company networks and systems. Unfortunately for all of us, there are a lot of vendors on underground hacker markets that sell those credentials for a laughably small amount of money.
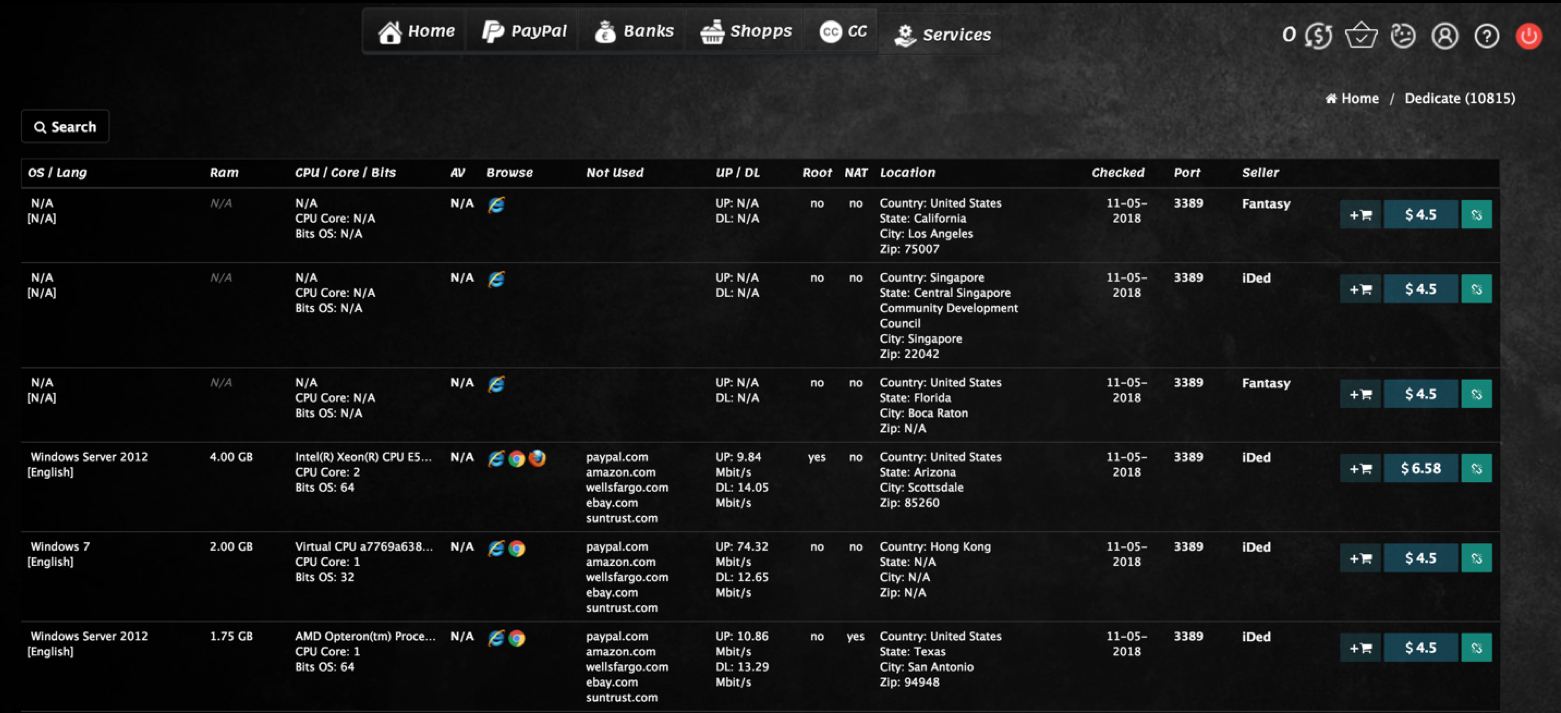
Some of these computers are part of critical systems. Case in point: McAfee researchers have recently discovered that access linked to security and building automation systems of a major international airport could be bought from these sellers for as little as $10!
What is RDP?
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft. It provides a user – usually a system administrator – with a graphical interface to connect to another computer over a network connection.
To establish the connection, the admin must run RDP server software on his or her system, and the target computer must have RDP client software installed. Client software exist for most versions of Windows, but also for other widely used computer and mobile operating systems.
Research discoveries
The researchers have analyzed the offerings of eight underground shops that sell RDP access credentials to those willing to pay for them. Once criminals gain access to the systems, they can use them to send spam, mine cryptocurrency, spread ransomware, and steal data and credentials.
The advertised systems range from Windows XP through Windows 10, as well as those running Windows IoT (formerly Windows Embedded) – usually PoS kiosks, announcement boards, parking meters, thin clients, etc.
“Prices ranged from around US $3 for a simple configuration to $19 for a high-bandwidth system that offered access with administrator rights,” the researchers noted. The sellers also offer buyers how-to guides and tips on how to use the RDP access and how to make sure their presence on it remains undetected for a while.
Among the systems for sale the researchers have also found many that belong to governments, health care institutions (hospitals, nursing homes, suppliers of medical equipment), municipalities, housing associations, and so on. These systems may hold much sensitive information and, if interfered with, can temporarily disrupt the functioning of these organizations.
An example of this is a Windows Server 2008 system offered for sale in April for a mere $10. The seller showed just part of its IP address, but that was enough for researchers to pinpoint (with the help of Shodan) the owner of the system: a major international airport.
Further research revealed that the compromised system had three user accounts available. One was the admin account, but the other two were associated with two companies specializing in airport security (security and building automation, and camera surveillance and video analytics).
“We did not explore the full level of access of these accounts, but a compromise could offer a great foothold and lateral movement through the network using tools such as Mimikatz,” the researchers added.
How to secure RDP access?
There is no point of implementing state-of-the-art security solutions if a backdoor such as an insecure RDP connection is left open, the researchers noted, and advised organizations to regularly check which services are accessible from the outside and how they are secured.
For securing RDP connections and thwarting brute-forcing hackers, the researchers advise using long and complex passwords and 2FA, disallowing RDP connections over the open Internet, and blocking IPs that have too many failed login attempts.
Regularly checking event logs for unusual login attempts is also a good idea, they say, and so is using an account-naming convention that does not reveal organizational information.
McAfee has notified the identified victims about their compromised computers.