Intel offers to pay for Spectre-like side channel vulnerabilities
Intel is expanding the bug bounty program it started last March, and is raising considerably the awards it plans to give out for helpful vulnerability information.
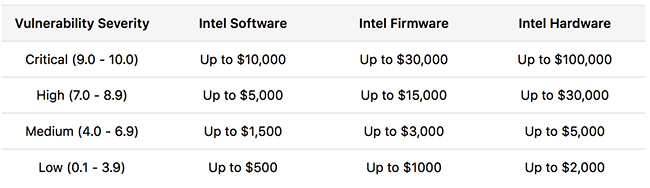
Where information about critical vulnerabilities in Intel software, firmware and hardware could have previously been rewarded with up to $7,500, $10,000 and $30,000, respectively, now the bounties in those same categories go up to $10,000, $30,000 and $100,000.
A new bug bounty program for side channel vulnerabilities
The company is, simultaneously, starting a new bug bounty program focused specifically on side channel vulnerabilities, i.e., vulnerabilities that are rooted in Intel hardware but can be exploited through software.
For information about these new Spectre-like holes the company is ready to cough up as much as $250,000, if they prove to be critical. That program is open until the end of the year (Dec. 31, 2018).
And, finally, while before the bug bounty program was invite-only, the company is now calling for all security researchers to participate.
“We will continue to evolve the program as needed to make it as effective as possible and to help us fulfill our security-first pledge,” said Rick Echevarria, VP and general manager of Platform Security at Intel Corporation, referencing Intel CEO’s promise – in the wake of the revelations of the Meltdown and Spectre bugs in the company’s silicon – of “doing security better.”
Whether or not the whole Meltdown and Spectre issue will end up impacting the company’s bottom line greatly is still unclear, but it sure seems that they’ve realized that they have to do everything in their power to regain users’ trust.
More information about the bug bounty scope and reporting requirements can be found here and here.
One of the non-negotiable requirements is that the vulnerability report must be encrypted with GnuPG or PGP using the Intel Product Security Incident Response Team public PGP key.