Laying the foundation for a proactive SOC
Most companies are trying to shift their Security Operations Center (SOC) from a reactive to a proactive posture.
To do that, the analysts’ reaction to security events must become swift, and investigation of security alerts and incidents must become more efficient. Once high effectiveness is achieved, the analysts can concentrate even more on hunting and detecting threats within the network before they become a problem.
Based on the interest our recent article on getting a start on cyber threat hunting has garnered, we’ve decided to do a deeper dive into Sqrrl Enterprise, and the concrete value it can bring to alert and incident investigators.
A force multiplier
A successful information security investigation depends on the evidence that can be gathered, so robust and diverse evidence sources (logs, SIEMs, etc.) are a must. But they won’t be of much help if the evidence cannot be easily searched and reviewed.
Sqrrl’s Security Behavior Graph makes hunting and investigations simpler and more effective, a “force multiplier”
Sqrrl’s visual Security Behavior Graph, which is based on a linked data model that displays user and entity activity on a network and the relationships between them, is what makes this solution an effective force multiplier:
1. It allows analysts to address 3 or 4 events in a single investigation, and provides unmatched context to quickly and clearly determine whether an alert is a false positive or not. This simplifies their work and saves their time, as well as that of the CSIRT who would otherwise waste it on investigating alerts that should not have been escalated.
To obtain sufficient clarity, analysts must be able to investigate an alert and determine both the impact that a potential incident could have and the confidence with which it was generated. This includes assessing the state of their IT infrastructure and gathering additional data about endpoints, applications, and network traffic. Without the right tools, this process is extremely complicated and time consuming.
2. It eliminates time consuming processes to manually fetch data, normalize, and correlate it, so that analysts can answer the following questions: “What other assets and what other activities were involved in the attack?” This dramatically improves alert resolution times.
3. Finally, it gives analysts a full picture of all the attack – tactics, techniques and procedures used – 20 times faster.
Information is just a few clicks away
Sqrrl is designed to simplify various types of hunts for both experienced and inexperienced analysts, and offers the same help to analysts tasked with incident response.
For example: You discovered that a host on your network has communicated with an IP address associated with a recent malware campaign, and you want to determine the nature of the communication. Unfortunately, it’s encrypted. So what other data points do you have available to pivot to from the IP address you have?
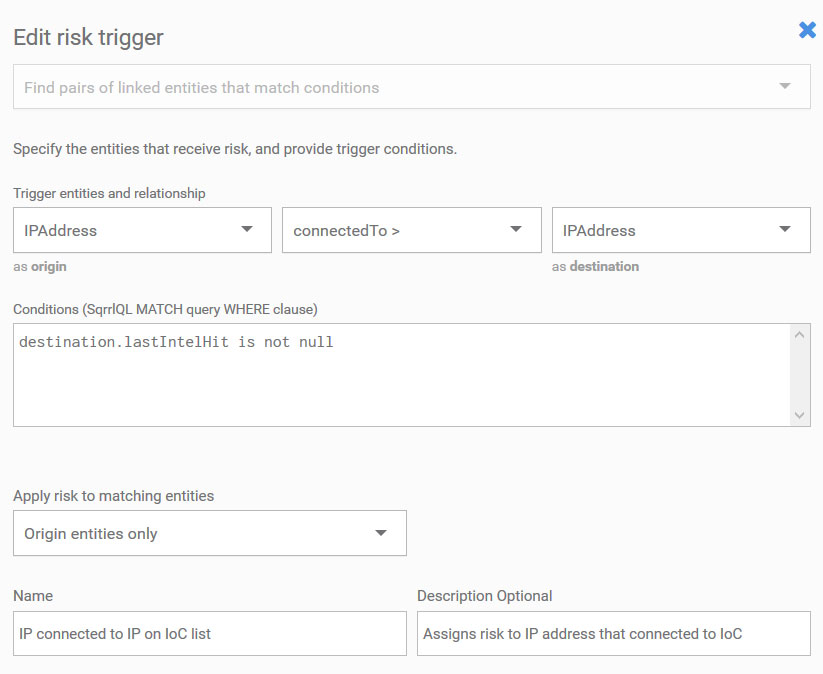
Custom Risk Trigger to add risk to an entity (IP address) match with Intel list
More experienced analysts could offer a few answers to that question, but those that are less familiar might not know them all.
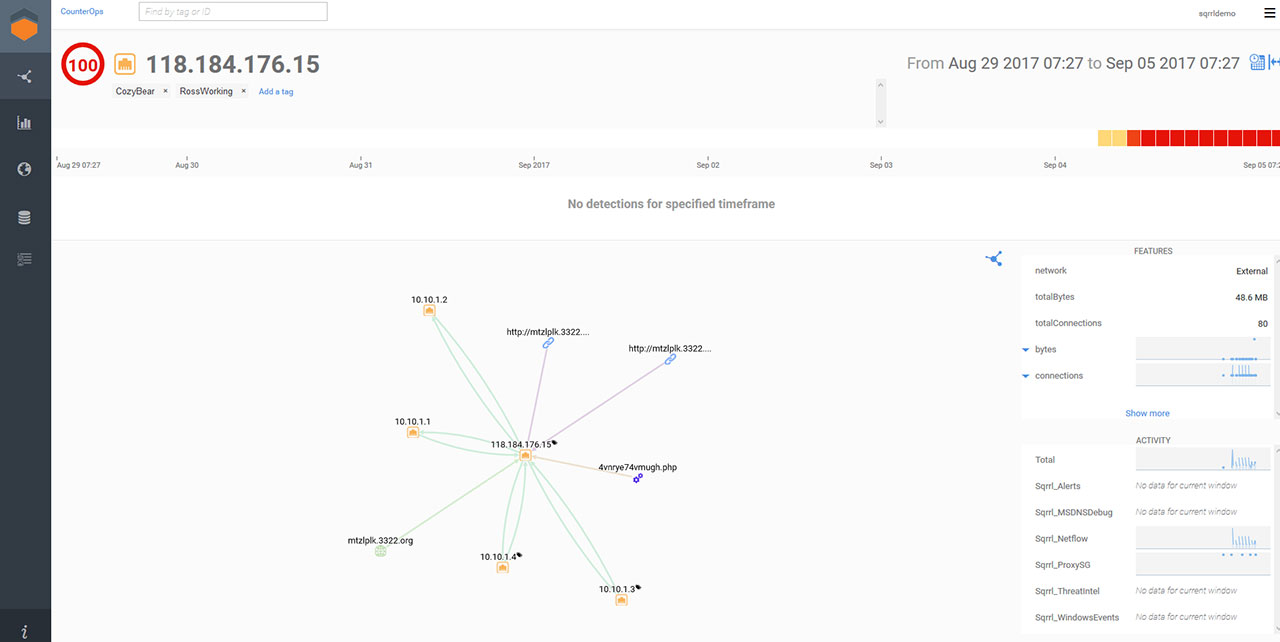
Starting with just the IP address in a static view we can see all connections and associated entity relationships
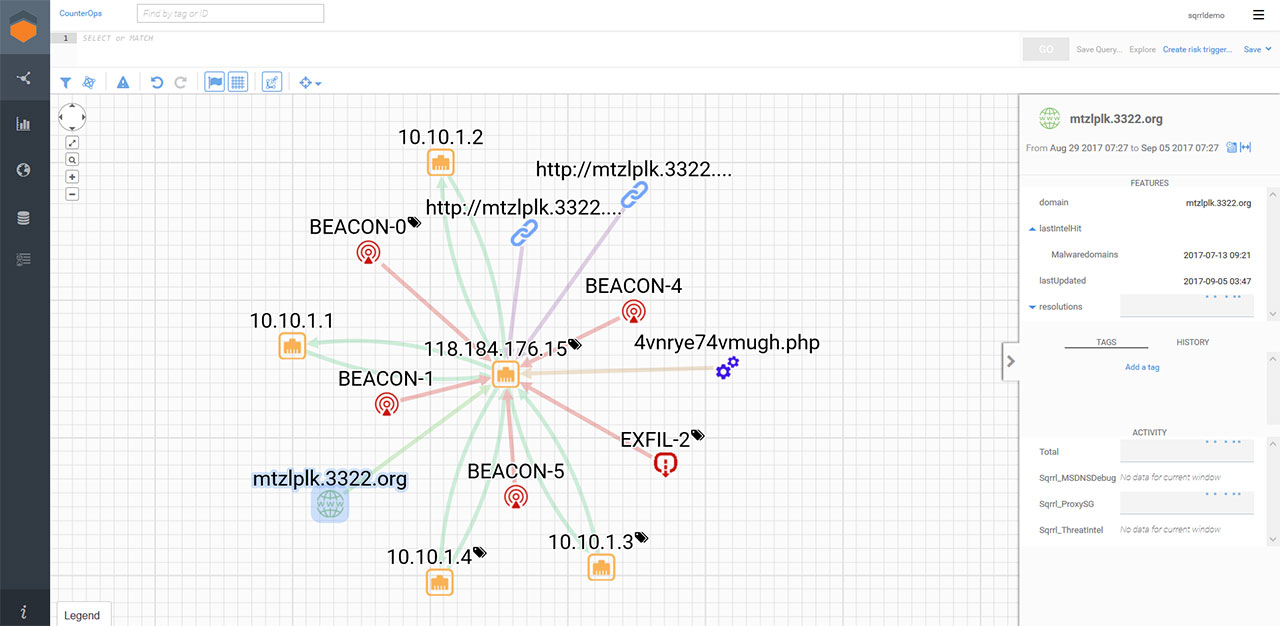
The we can go to explorer view and expand detection on the IP. I highlighted a malicious domain to show case the intel hit, but I did not draw an arrow to point at it
With Sqrrl, the answers are right there – the platform provides all the pivots that are available for a specific input. Not only that: all the pivots have a sense of direction, which adds context to them and ultimately helps analysts answer questions that will lead them towards meaningful conclusions.
Other questions Sqrrl can answer quickly is whether the data they are analyzing shows up in any of the other data sources available to the analyst, whether a suspicious looking domain name resolved by a friendly host communicated with the same IP address that is now associated with it, and so on. No more submitting a string of queries to get to the information you need – a few clicks will suffice now.
The same process length is required to get at the “real story” behind each piece of evidence.
For example: You investigated a suspicious domain and found no sign of malicious activity from the associate IP address. But, did the domain at that time have the same IP address as it has now? Getting this information from a traditional SIEM requires making large queries to multiple data sources. Sqrrl can answer that question after a few clicks, and you can continue the investigation by checking out the other IP addresses that were associated with it when one of your hosts contacted it.
Similar investigations can be made to discover whether a real owner of an account is behind the username authenticating to a system, or whether malicious attachments with different names are actually the same file. With Sqrrl, expanding the scope of investigations takes a lot less effort and time than before, which also means it is more likely to happen.
A similarly easy-to-perform expansion can be made to see whether a suspicious or malicious indicator can be found on other devices. Such a search can, for example, uncover infected hosts that simply haven’t yet executed the malicious file.
Here I just selected skype.exe, which doesn’t have to be malicious, entered explorer mode and expanded out connection resolutions to the hosts. I removed one host that did not resolve to an IP address.
Other variations of these attack scope expansions can include searching through a broader array of data sources, a larger time span, or a larger array of the attack surface area (e.g. more hosts). Sqrrl effectively facilitates the collection of these puzzle pieces strewn across the company’s networks and assets.
Improved defense
How often your analysts will be able to turn to threat hunting instead of always being two steps behind the attackers depends a lot on the tools you give them.
With the right tools, they’ll be able to breeze through the alerts and evidence and make critical assessments and decisions much more quickly. They will be able to cover much more ground than before, while expending less effort and time.
Such an increase in efficiency can only be good for both the organization and the analysts themselves: they will be able to dedicate more time to improve their threat hunting knowledge and capabilities, and use them to become even better defenders.