Complete and continuous cloud infrastructure protection
 In this podcast recorded at Black Hat USA 2017, Hari Srinivasan, Director of Product Management at Qualys, talks about the challenges involved in securing clouds, and explains how to gain complete visibility and security of your cloud infrastructure using Qualys CloudView.
In this podcast recorded at Black Hat USA 2017, Hari Srinivasan, Director of Product Management at Qualys, talks about the challenges involved in securing clouds, and explains how to gain complete visibility and security of your cloud infrastructure using Qualys CloudView.
Here’s a transcript of the podcast for your convenience.
Hello there, my name is Hari Srinivasan, I’m the Director of Product Management with Qualys. Qualys recently launched Qualys CloudView. Qualys CloudView provides you with comprehensive visibility and continuous security of public cloud infrastructure. In today’s podcast I’m going to detail out what you probably might be missing out in the cloud and how Qualys can help you to gain visibility and security of your cloud infrastructure.
There’s a tremendous amount of growth in the cloud. Almost 92% of data center traffic will be cloud-based by 2020 says a global cloud index forecast. When you move your infrastructure and workloads into cloud, you are responsible for securing them. There’s a shared security responsibility model between you and the public cloud provider.
The shared security responsibility model varies by different services used in cloud. For IAS, you control more of the resources so you take ownership of the security of those resources starting from the operating system and up. For platform as a service, where you’re provided with the software directly by the provider, the provider takes care of operating system and virtualization layers below. You take care of data and the application security. For software as a service, the provider takes care of the complete stack and you get the responsibility of securing the access in your organization who gets to see it.
Recently, there has been news about American alter data being leaked by a firm contracted by RNC. Close to 190 million voters data has been leaked in this process. These are all due to an unsecured public cloud storage account.
This should make you think about the number of resources and different resource types you are using in the cloud that you probably are not accounting for. In addition to the standard resources like instances database and storage, you also need to secure access management, people who get access to your cloud and their security around their access credentials, network access, administrative access of who gets through to what in cloud.
You need to know about these additional resources and the security portion of these additional resources in order to keep your cloud infrastructure secure in overall basis.
So, let’s look at what are the challenges in securing clouds. To begin with, it’s a lack of visibility. Knowing what resources are being used in cloud by different business units within your enterprise and also business applications that are adapting cloud. Two is a lack of control, the ability to define and assess security for different types of resources, and do audits to keep things in check on a time to time basis. Number three is agility. A cloud is elastic in nature. It grows and shrinks depending on the demand. You need to have tools which keep up with this agility and also integrate into new development processes like DevOps.
Before I drill down into the solution, let me give you two personas in the organization with whom you can relate to.
Dave, the cloud architect who wants organizations to utilize cloud, he would like to know what organizations are using cloud, what applications are using cloud and how secure are their practices.
The second persona is Sally. Sally is from the InfoSec team. Sally is used to do vulnerability management and compliance for her regular environments. Taking that program into cloud, now she’s also introduced to the notion of having other resources in the cloud, so she would like to kind of have a view of existing vulnerability management and policy compliance program in conjunction with the other resource types and understand the security of the cloud overall. At the same time, Sally wants to also automate the processes as a part of the DevOps initiative in the organization.
Qualys CloudView provides answers to both of these personalities. For Dave, it provides him with visibility of what is going on in the cloud, which business units are using cloud and which applications are using cloud. And for Sally, providing her a view of the security posture of cloud in context of the security program which she’s already been following, and providing her with APIs to integrate the security solution for the entire cloud into her DevOps process.
Qualys CloudView provides you with unparalleled visibility and continuous security monitoring across a public cloud infrastructure.
Let me explain the CloudView solution in three parts. To begin with, it enables organizations to continuously monitor and secure public cloud infrastructure against misconfigurations and malicious behavior, and also non-standard deployments:
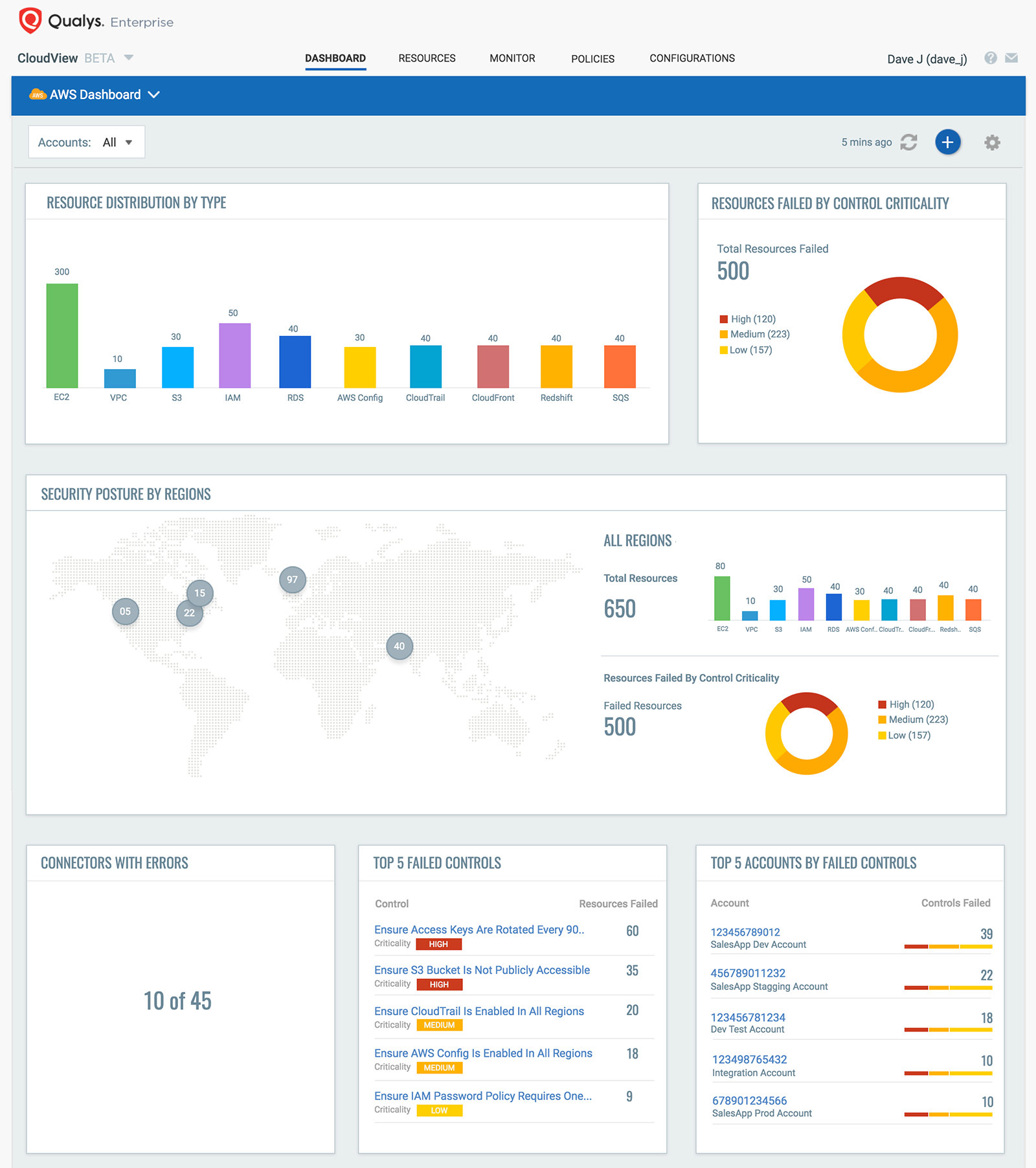
- It discovers assets which are in their cloud. These assets are beyond the regular hosts of instances of virtual machines. It looks a lot more other resource types like VPCs, security group, storage buckets, IM users, cloud trail, cloud front, relational database services across multiple clouds like AWS, Azure and Google.
- As soon as the data has been collected, it applies security policies on those data to do configuration checks. It runs this in a continuous fashion and as the cloud environment changes, it pulls the data and applies security policies.
- It also provides you with remediation and security insight of these resources. It gives you information about the resources and its association and provide you with recommendations to remediate any identified vulnerability based on misconfiguration.
All of these functionalities is also completely supported via REST APIs. The APIs allow you to integrate with some solutions and also with your end-to-end processes which you follow like ticketing and remediation.
To summarize, Qualys CloudView enables organizations to look into their cloud deployments, get the complete visibility of all resources in the cloud, and provides you with the continuous security to keep cloud environments in check as it grows.
For the first version of this product, Qualys is announcing availability in AWS cloud, it provides you with an ability to do policy check on CIS. Further you can generate reports if you are following PCIDS’s, NIST, HEPA, ISO 27001. All of this is available as a part of a new model, and if you’re using existing products for vulnerability management and policy compliance from Qualys, it pulls on the data and makes it available in context after other cloud resources, enabling you to prioritize the threats effectively.
Thank you for listening into this podcast. I hope this enabled you to look beyond the standard resource types which you would normally use in a cloud, and you look forward for security solutions to secure them against threats and risk.