Attackers turn to auto-updating links instead of macros to deliver malware
SANS ISC handler Xavier Mertens has flagged and analyzed a malicious Word file that, somehow, is made to automatically download an additional malicious RTF file, ultimately leading to a RAT infection.
What is curious about this particular attack is that it uses an approach that Mertens has never encountered before: the file exploits a Microsoft Word feature that can make files automatically update links included in them as soon as they are opened.
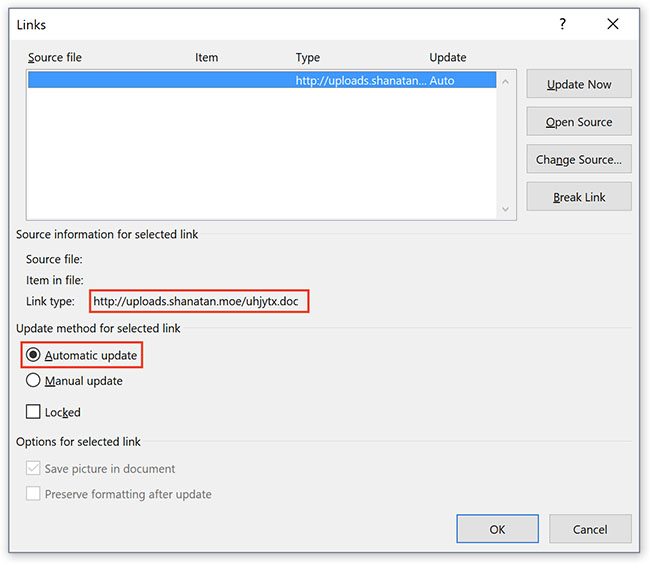
“The infection vector was classic: The document (‘N_Order#xxxxx.docx with 5 random numbers) was received as an attachment and has a VT score of 12/59 this morning. The file has an embedded link to another document which is a malicious RTF file that tries to exploit the CVE 2017-0199,” Mertens discovered.
The Word file tries to access the malicious RTF file and, if it succeeds, the latter downloads a JavaScript payload, which creates a shell object to spawn a PowerShell command and download a malicious PE file – the Netwire RAT.
Mertens told me that the link update is triggered without user interaction or without a prompt or warning to the user that such an action will be undertaken – something that, by all accounts, should not happen.
On the other hand, the Malwr malware analysis service shows that the file does require the victim’s approval to update the document with the data from the linked files:

Recent attacks using similar approaches
Interestingly enough, Trend Micro researchers have also recently spotted the CVE 2017-0199 vulnerability being exploited.
In that attack, the delivery mechanism is the same (email attachment), the booby-trapped file is a PowerPoint Open XML Slide Show (PPSX) file, and the final payload is similar (a RAT with keylogging capabilities). The final payload is run with the help of the PowerPoint Show animations feature.

Finally, all of this reminded me a bit of a relatively new PowerPoint malware delivery technique tested by spammers. In that case user interaction was definitely required: the victim had to hover with the mouse’s pointer over the link in the PowerPoint file in order to trigger the download:

“Time will tell whether this new infection vector gains popularity among the criminal element. The fact that it does not need a macro is novel and triggers on mouse activity is a clever move,” Malwarebytes researcher Jérôme Segura noted at the time. “There is no doubt threat actors will keep on coming up with various twists to abuse the human element.”
Perhaps these latest attacks are an evolution of that one?
In all the cases, though, it’s pretty obvious that the attackers are targeting companies, and that their ultimate goal is to get their hands on information that will allow them to steal money from the victims’ accounts.