Hackers hosted tools on a Stanford University website for months
Compromising legitimate websites and the web servers that store and deliver them is a time-honoured tactic of opportunistic hackers, and a failure to keep them out can result in the servers hosting phishing and scam pages, spam mailers, exploit kits, or malware.
Sometimes, these vulnerable servers are abused by different hackers, who vie for sole control or are simply content to share the asset.
Case in point: the website and web server of the Paul F. Glenn Center for the Biology of Aging at Stanford University (at glennlaboratories.stanford.edu).
According to Netcraft’s Paul Mutton, the site is now clean, but for many months, it was a playground for hackers.
The compromise
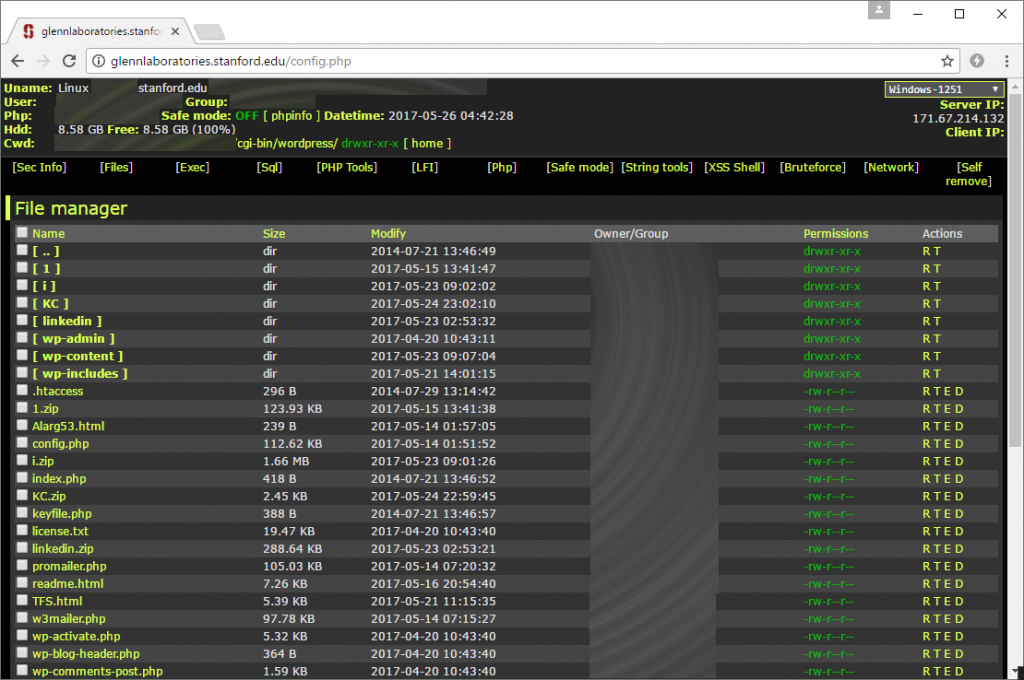
It was first compromised in January 2017, when one attacker managed to install a PHP web shell into the top-level directory of the website.
A web shell is a small program that can be opened through a browser by visiting a specific URL, and it allows users to execute common tasks (view, edit, delete, upload files, execute shell commands, etc.) on the compromised web server.
The tools
It took over four months for other attackers to spot the accessible (to anyone) web shell, but once they did, they used it to start uploading their own tools:
- A new webshell with many more features that the first one. This one was also accessible without a password by anyone.
- A HTML files containing a defacement page with the hacker’s moniker
- Two mailer scripts
- A Chinese HiNet phishing site
- Another defacement page
- Phishing sites that targeted users of Office365 and LinkedIn
- A generic phishing page
- A SunTrust Bank phishing page, and so on.
There are several things that indicate that the attackers deploying and using these tools might not be one and the same person: different defacement pages, the removal of some phishing content at a later date, the different email addresses to which the phishing pages send the stolen login credentials.
Of course, it is difficult to be absolutely sure that this was a case of different hackers using the same compromised web server, but Mutton says that “failing to notice and remove the hacking tools could well have compounded the problem by facilitating the more recent compromises.”