Attacks within the Dark Web
For six months, Trend Micro researchers operated a honeypot setup simulating several underground services on the Dark Web. The goal of their research was to see if those hidden services will be subjected to attacks.
Hidden services under attack
The setup consisted of:
- A closed, invite only black market
- A blog offering customized services and solutions for the Dark Web
- An underground forum that could be used only by invited, registered members
- A (misconfigured) private file server that allowed access via FTP and SSH.

Each honeypot sported one or more vulnerabilities, to make successful attacks likely. The researchers automatically recorded all logs after every compromise and restored the environment to a clean state each day, to await more attacks.
What the researchers discovered
One discovery that was made pretty quickly is that the attack did not come only from the Dark Web.
“Tor proxies like Tor2web made Tor hidden services reachable without requiring any additional configuration from the public internet. Our honeypot was automatically made available to traditional search engines, and implicitly dangled as a target for automated exploitation scripts,” the researchers shared.
In one month, the number of attacks spiked to over 170 per day – most of them successful.
“The majority of these attacks added web shells to the server, giving the attacker the ability to run system commands on our honeypot. This allowed the addition of other files, such as web mailers, defacement pages, and phishing kits,” they noted.
Using compromised hidden services for DDoS or spam attacks is a sweet deal for attackers, as the origin of the attack is automatically anonymized by Tor.
After they began filtering traffic from Tor proxies, the attacks decreased, and were limited to attackers from within the Dark Web.
Manual attackers
Unlike attacks from the “outside,” which were mostly performed with automated tools, Dark Web attackers preferred to tread more slowly and cautiously, and their attacks were manual.
“For example, once they gained access to a system via a web shell, they would gather information about the server first by listing directories, checking the contents of databases, and retrieving configuration/system files,” the researchers explained.
“These manual attackers often deleted any files they placed into our honeypot; some even went ahead and left messages for us (including ‘Welcome to the honeypot!’), indicating that they had identified our honeypot.
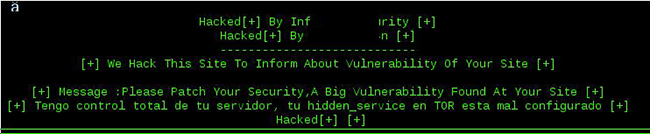
Aside of defacements that often functioned as promotion for competitor sites, the attackers also went after confidential data stored on the honeypot FTP file server, tried to hijack and spy on the communications originating to and from the honeypots, and targeted the forum application.