Data breach activity reaches all-time high
With over 1,200 breaches and over 3.4 billion records exposed, 2017 is already on pace to be yet another “worst year on record” for data breach activity, according to Risk Based Security.

W-2 phishing
“The trends that drove the extraordinary activity in 2016 are continuing unabated in 2017” said Inga Goddijn, Risk Based Security’s Executive Vice President. “We have seen the return of widespread phishing for W-2 details, large datasets continue to be offered for sale and misconfigured databases remain a thorny problem for IT administrators”.
Targeting information useful for filing false tax returns is not a new practice and neither is phishing unsuspecting employees in order to obtain valuable information. However the practice of emulating a trusted party and requesting copies of W-2 forms has clearly become a favorite money making scheme for the first quarter.
BEC scams
The trend came to prominence last year, when more than 60 organizations fell for the specialized phishing scam in Q1 of 2016. Known as Business Email Compromise, or BEC, the practice generally involves sending an email impersonating a trusted colleague or business partner, requesting either a funds transfer or personal information. Despite the experience in 2016 and warnings from the IRS in January and February of this year, over 200 organizations fell for the scam in first 3 months of 2017.
“What I find especially striking about these breaches how is reluctant organizations are to disclose the number of W-2 records lost in the phishing event,” said Goddijn. “When it comes to consumer or medical data, chances are good the number of records compromised will be reported. But in the case of employee W-2 data, the severity of the event is often swept under the rug.”
Sale of large datasets
Another 2016 trend that continued into Q1 2017 is the sale of large datasets. One particular seller was especially active this past quarter, offering for sale various username and password combinations gathered from 11 different organizations and impacting a whopping 1.5 billion records in total. The validity of the data has not yet been independently verified, raising some concerns about the accuracy of the information being sold. However, there is also no indication the data was gathered from prior data dumps or reason to believe the data is anything other than as represented by the seller. What is clear is that as long as organizations rely on the traditional username and password combination for authentication, datasets like these will continue to have value to malicious actors.
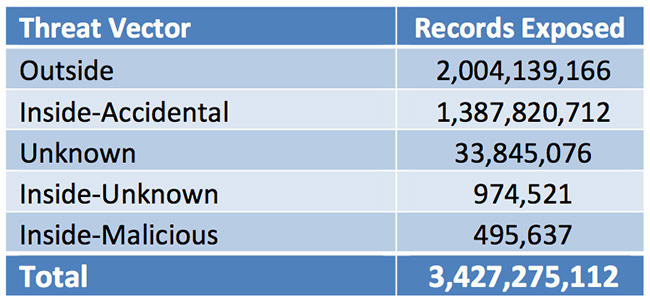
First three months of 2017 exposed records by threat vector
Misconfigurations
Much like phishing for W-2 data, the problem of misconfigured database installations and Rsync services continues to contribute significantly to overall breach activity. Although researchers have been warning of the problem for years, the ease of finding and accessing the data has caught the attention of individuals with less than honorable intentions. 2017 started with a wave of extortion demands, targeting open, unsecured MongoDB instances.
Exactly how many databases were scraped, deleted, held for ransom or otherwise tampered with remains unknown. It is clear that what started as a quick money making endeavor quickly devolved into dumping the contents of the databases on file sharing forums. Organizations such as Science Mobile – the makers of the popular Wishbone app – RankWatch and Careerlister saw millions of records taken from open MongoDBs and later dumped on the Internet.
In the most striking example of misconfiguration problems, River City Media, LLC, an organization with a somewhat checkered reputation, accidentally exposed 1,374,159,612 records containing personal information as well as sensitive internal business documents in a faulty Rsync backup. Not only is this the largest misconfiguration incident on record, it is now the single largest breach disclosed through Q1 2017.
“With breach activity showing no signs of slowing down, it’s become more important than ever to understand the drivers behind data loss. This is especially true when it comes to understanding the risk factors facing our third party business partners. Monitoring for leaked credentials, verifying security hygiene and getting alerted to new breach activity are now critical components of the vendor risk management process,” added Goddijn.