How can we build a secure IoT world?
We have almost daily proof that the Internet of Things, as it is now, is a minefield of security issues that are just waiting to be exploited.
The unfortunate reality is that those IoT providers and manufacturers that concentrate on functionality instead of security and privacy are the ones that will make the most money, and be therefore more likely to continue doing business.
Another lamentable reality is that governmental and other organizations that should push for better cyber security strategies, policies, regulations and standards are severely lagging behind.
The bigger picture
What will it take for us to build a trusted IoT ecosystem?
For one, countries will have to develop national IoT strategies and include in them guiding principles for IoT security and privacy. Then, all industries that implement IoT devices – and there are many – will have to prioritize IoT security, and industry organizations will have to get involved in building and maintaining robust IoT security policies, laws and regulations.
Standards organizations and alliances will have to work on proposing and designing security technology standards to tackle IoT security challenges at a faster pace. Some of them – the National Institute of Standards and Technology (NIST) and the Internet Engineering Task Force (IETF), for example – have already started pushing out security frameworks and cybersecurity guidelines for the IoT, and working on making applicable protocols secure, but detailed technical standards that can guide the implementation in industries are still scarce.
Finally, all of them together with academia and developers (both of closed and open source solutions) must cooperate and share knowledge. As experts from Huawei and the Spanish National Cybersecurity Institute noted in a recently published whitepaper, “no enterprise or organization can resolve IoT security issues alone.”
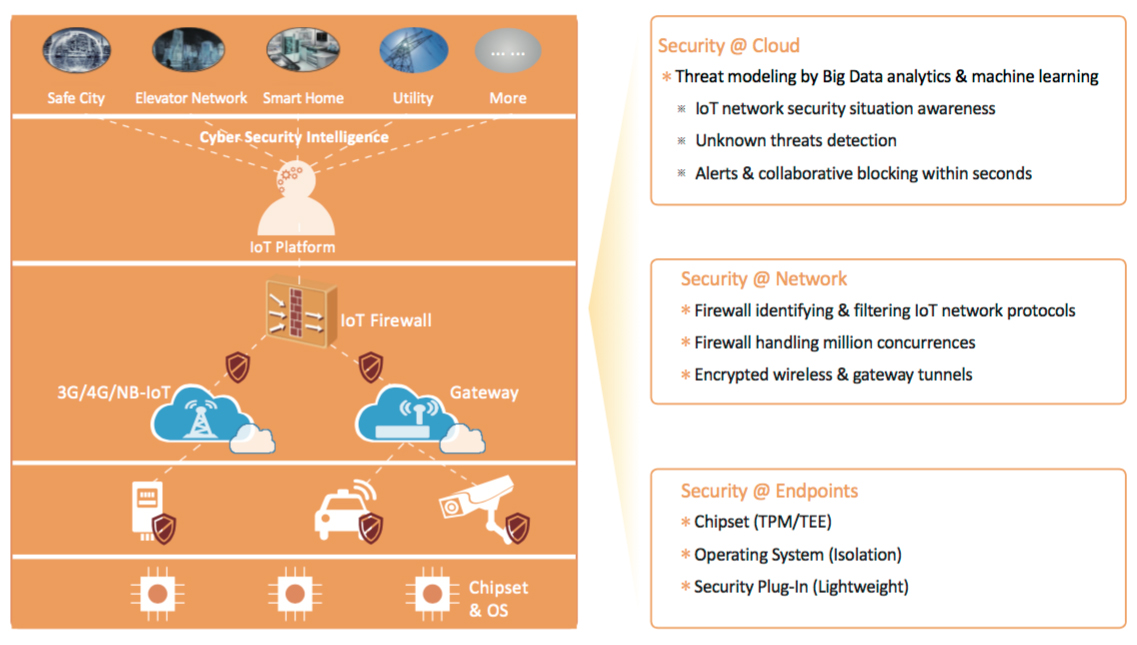
We must build a multi-layered, end-to-end secure IoT world
IoT security risks and threats are many, and privacy is the biggest legal challenge tied to IoT deployment. Security and privacy protections should be built in from the very start, and involve better decisions and solutions for every step of the development and deployment process.
“IoT security is manifested in chips, devices, and their operating systems, networks, management platforms, apps, and enterprise operation,” they experts noted. “In addition to security protection at each layer, a comprehensive end-to-end defense system is developed based on the interdependence of the device, pipe, and cloud.”
Secure chips can provide hardware-level encryption and isolation, secure boot and software and firmware signature support. The OS should provide memory protection and isolated scheduling mechanisms, privilege separation and process isolation, trusted identity authentication, secure firmware upgrade, Internet service access control, encryption and decryption, and key management.
IoT endpoint security requires a new security architecture which will offer physical security (from the environment), access security (to protect endpoints from being used as stepping stones to attack critical network nodes), running environment security (software signatures, access whitelisting, etc.), service data security, and unified management (during the complete lifecycle of the device).
Network layer security involves old security mechanisms and new security requirements for IoT communication technologies, and the many proprietary protocols and industrial control networks. Also, antivirus and APT defense.
The main factor when it comes to platform and application security is the management is personal data and its secure storage. And finally, to complete it all, Big Data security analytics platforms are needed to provide network-wide situational awareness, monitoring, visualization and security defense.
There are many security practices that can help with each step of the development, deployment, operation and maintenance processes, and the whitepaper contains a helpful list. It also includes an overview of typical IoT security cases (smart home, smart grid, elevators).