Phishers’ new social engineering trick: PDF attachments with malicious links
It is – or it should be – a well known fact that attackers occasionally email potential victims with PDF attachments containing malware or exploit code.
But the latest attacks through PDF attachments are geared towards pushing users to enter their email account credentials into well-crafted phishing pages.
Attack variants
Microsoft security experts saw a lot of variants of the same attack, and they all start with spoofed emails supposedly delivering asked-for documents.
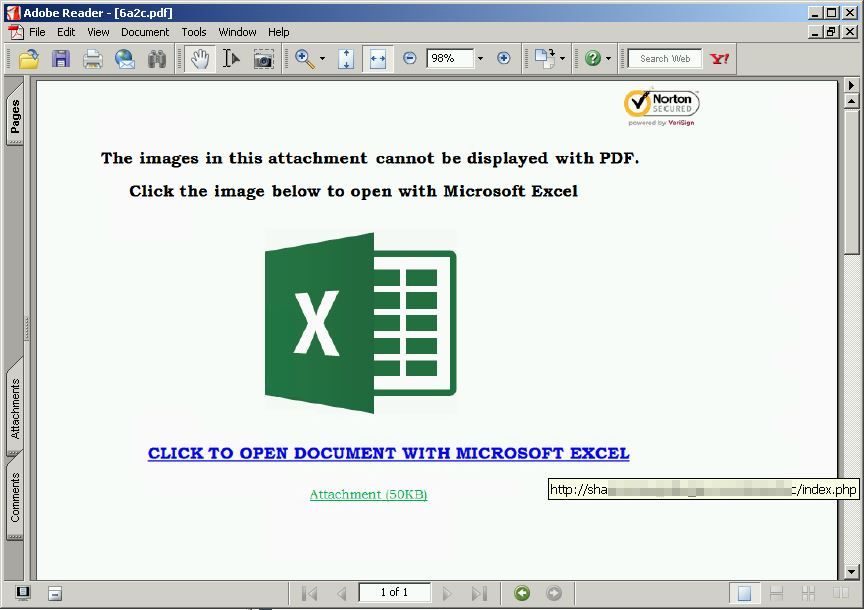
In one variation, the PDF makes it look like there has been an error, and the document can only be displayed with Microsoft Excel. But instead of actually opening it with their own software, potential victims are urged to open it by following the link offered in the PDF:
If they do that, they will be redirected to a web page that makes it seem like the document can only be opened if the user signs in with their email credentials.
In another variant, the PDF urges users to click on a link that will supposedly allow them to view a Dropbox-hosted document online. Again, they are redirected to a phishing page that “allows” them to view the document only if they log in with their email credentials:
In this particular case, when they enter their credentials they are actually shown a decoy PDF document, making it more likely they won’t notice right away that they have been phished.
What to be on the lookout for
“Social engineering attacks are designed to take advantage of possible lapses in decision-making. Awareness is key; that is why we’re making these cybercriminal tactics known,” Microsoft’s Alden Pornasdoro explained.
“In these times, when we’re seeing heightened phishing attacks with improved social engineering techniques, a little bit of paranoia doesn’t hurt. For instance, question why Adobe Reader is trying to open an Excel file. Ask why Dropbox is requiring you to enter your email credentials, not your Dropbox account credentials.”
Microsoft Edge users have a slight advantage here, as the Microsoft SmartScreen technology blocks these phishing pages from loading. Firefox users who have updated to the last stable version could be helped by the fact that the browser now flags HTTP login pages as insecure.