Net Cease: Microsoft researchers unveil anti-reconnaissance tool
Microsoft researchers Itai Grady and Tal Be’ery have released Net Cease, a PowerShell script that prevents attackers who have already compromised an endpoint from getting information about other targets within the same corporate network.
The idea behind the script is to make attackers’ lateral movement on the network more difficult.
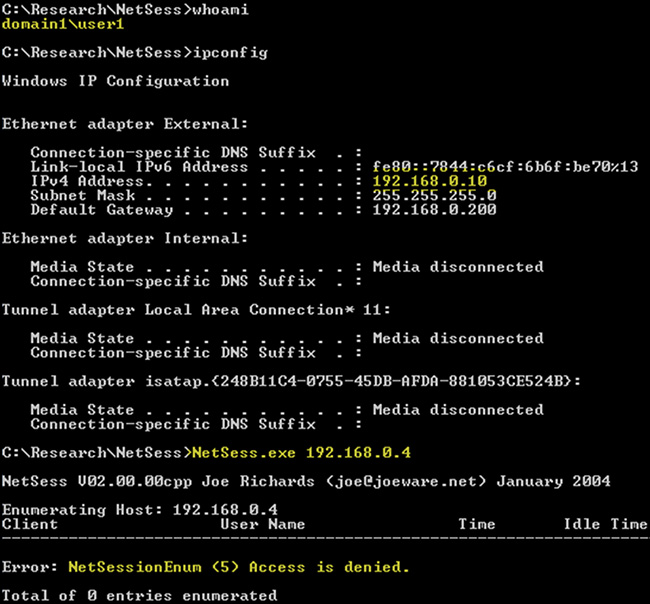
Non-admin user gets access denied calling NetSess remotely after Net Cease was deployed on the target machine
This type of reconnaissance can be performed by applying the Server Message Block (SMB) Session enumeration via the NetSessionEnum method against the domain controller (DC), and attackers can get valuable information about the next target.
In fact, there are already penetration testing tools out there that have automated this type of search.
Net Cease works by changing the default permissions for the NetSessionEnum method to limit the number of domain users who are able to execute the method remotely.
“The NetCease script hardens the access to the NetSessionEnum method by removing the execute permission for Authenticated Users group and adding permissions for interactive, service and batch logon sessions,” the creators explained.
“This will allow any administrator, system operator and power user to remotely call this method, and any interactive/service/batch logon session to call it locally.”
The script is extremely easy to use and works on Windows 7, 8, 10 and Windows Server 2012, 2008 and 2003.
“Note that hardening NetSession and hindering attackers’ ability to abuse it does not damage defenders’ ability to detect the attack, as MicrosoftATA [Microsoft Advanced Threat Analytics] detects failed recon attempts as well,” the researchers added.