Automotive security: How safe is a next-generation car?
The vehicles we drive are becoming increasingly connected through a variety of technologies. Features such as keyless entry and self-diagnostics are becoming commonplace. Unfortunately, they can also introduce IT security issues.

When Chris Valasek and Charlie Miller demonstrated at Black Hat USA 2015 how they can remotely exploit vulnerabilities in Chrysler’s 2014 Jeep Cherokee, many thought it was interesting, but not a widespread problem. Turns out it was just the tip of the iceberg.
Time to patch your car?
This year we’ve learned that several automakers are plagued by a plethora of security issues:
- A group of researchers from ADAC, the largest automobile club in Germany and Europe, have demonstrated how the keyless “comfort locking” system used by most automakers on most modern cars provides no security against vehicle theft.
- The Mitsubishi Outlander hybrid SUV can be easily broken into by attackers exploiting security weaknesses in the setup that allows the car to be remotely controlled via an app.
- Security researchers have come up with a way to unlock hundreds of millions of cars from the Volkswagen Group, Alfa Romeo, Chevrolet, Peugeot, Lancia, Opel, Renault and Ford. The hardware tools required to pull off the attacks is cheap and accessible to practically everyone.
- Think premium brands are not at risk? Think again. Back in July we learned that BMW ConnectedDrive flaws could be misused to tamper with car settings.
Houston, we have a problem
Government institutions are taking notice. With a public service announcement compiled jointly with the Department of Transportation and the National Highway Traffic and Safety Administration, the FBI has announced that it finally considers car hacking a real and present danger, and so should the general public and vehicle manufacturers.
The automobile industry is beginning to realize they are unable to tackle mounting security issues on their own. Last month Fiat Chrysler Automobiles launched a bug bounty program. The biggest reward payout is still small, and amounts to only $1500, but I’m sure we’ll see an increase as potentially more damaging vulnerabilities are uncovered in all types of modern vehicles.
Members of the Automotive Information Sharing and Analysis Center (Auto-ISAC) released an overview of comprehensive Automotive Cybersecurity Best Practices developed as a proactive measure to further enhance vehicle cybersecurity throughout the industry.
The Automotive Security Review Board
Launched in June of this year, the Automotive Security Review Board (ASRB) is a non-profit industry consortium that came about due to the multifaceted objectives of removing barriers to the evolution of automotive innovation, without cybersecurity becoming an inhibiting factor.
“The industry has a great deal of respect for safety and the consequences of adding connectivity to modern automotive systems, yet is dealing with the challenge of adding connectivity to systems that were never intended to be connected as well as new technologies. We wanted to support these development efforts with design architectures that provided an appropriate level of security that anticipates both future needs and potential threats,” Steve Grobman, President of Intel’s Automotive Security Review Board, told Help Net Security.
Rather than approach the challenge with a backward facing posture, applying solutions based on present day threats and vulnerabilities, the ASRB is looking at where the auto industry is going, and looking at security proactively to get in front of potential exploits.
Threat evolution
If you’re in the information security industry, it takes you probably less than a minute to come up with several dangerous scenarios that can impact modern vehicles in the near future, some of them even life-threatening for the drivers.
With an increasing number of heavily connected vehicles taking the road, I wondered if there is anything car buyers can do to protect themselves. After all, not everyone has the knowledge, tools, and time to dedicate to exploring the security of their automobile after purchase.
“Safety is an absolute imperative, but just consider the convergence of connected cars with a trend such as ransomware. How much would you consider paying a cybercriminal to get to work for an important meeting? Would $250 be too much to pay to access your car and be able to drive to the office? Would you pay more?” asks Grobman.
“If we have millions of connected cars on the road, and cybercriminals infect tens of thousands of cars, dealerships will only be able to accommodate a limited number of ransomware car infections at any given time. Given the incentive structures around ransomware, and the tremendous number of potential targets, it’s not a stretch to imagine something like ransomware becoming as great a concern for automakers as the safety nightmare scenarios so often posed in this area,” he explains.
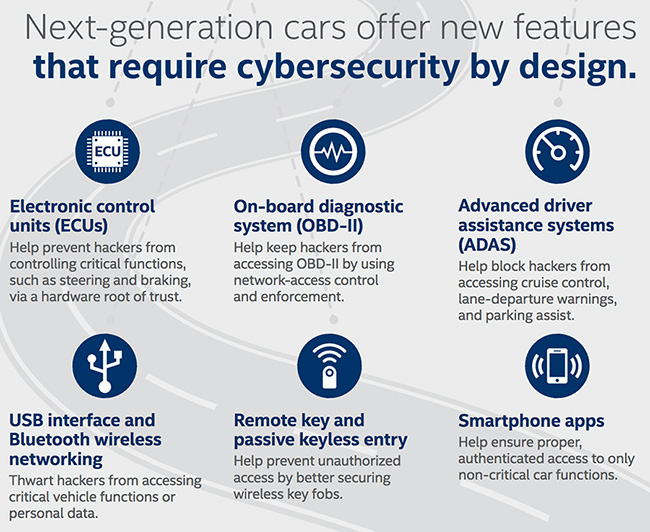
Making security a priority
It’s obvious vehicle manufacturers should implement more security into their development and testing processes, but what can make them upgrade security? If the payout for potential repercussions is lower than an investment in security, and there are no strict compliance guidelines, they have little incentive to do better.
“The challenge with using regulation as the driver for cybersecurity is that the threat landscape changes rapidly. Companies often invest in being compliant to guard against the previous generation of threats and in many cases are less secure because they could not optimize efforts for the highest risk areas. Getting the balance right between regulation and the flexibility to optimize for the highest risk threats is critical. The automotive industry will come to learn what other industries have learned about connected systems: manufacturers will need to account for security integrity as well as reliability,” says Grobman.
One of the biggest challenges of automotive security is that it’s about achieving security at a component level, but also achieving security at a systems level. It’s about doing so with an architecture that was never really built to assume that there would be rogue communications on the internal buses and networks of the automobiles.
“The automotive industry will have to make the transition that other industries have had to make since becoming connected. Automotive security will need to comprehend failure conditions, but also compromise conditions. Investments will follow these new business priorities, and profits will reward the technical priorities of getting security right,” concludes Grobman.