Impatient users saddled with malicious copycats of popular Prisma app
If an iOS app gains extreme popularity but still does not come in a version for Android, it can be practically guaranteed that malware peddlers and scammers will take advantage of users’ impatience, and offer fake, malicious versions of it on Google Play and third-party Android apps stores.
It usually happens with games, but any popular app will do. The latest example of this is the turn-photo-into-art app Prisma.
First released on iOS in June 2016, its popularity soared and it took almost two months for the Android version to be offered on Google Play.
But cyber crooks and scammers were quicker than that, and managed to produce and place their copycat apps.
“Most of the fake Prisma apps found on Google Play didn’t have any photo editing functionality; instead they only displayed ads or fake surveys, luring the user into providing their personal information or subscribing to bogus (and costly) SMS services. Some actually had very basic photo editing functionality but mainly served the user a stream of pop-up ads or displayed scareware activity to persuade the user their device was infected with malware,” ESET researcher Lukas Stefanko notes.
But, unfortunately, five of those apps also hid a downloader inside them, capable of downloading additional modules and executing them.
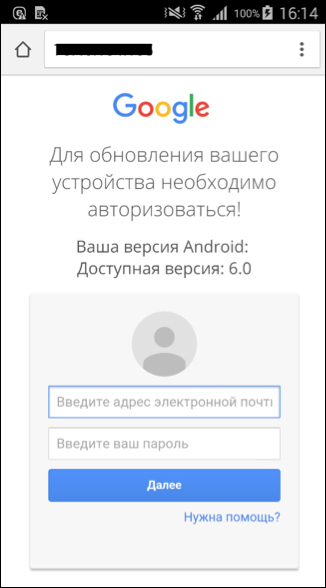
Among the modules were those that collected device and user info, but also phishing modules that went after users’ Google account credentials by displaying fake requests to update to Android 6.0.
According to ESET, all of those copycat apps have been downloaded by 1.5 million users, and the ones carrying a downloader by at least 10.000 of them.
While malicious app peddlers really don’t have to wait for this type of opportunity to come up, as many users can be fooled into downloading a copycat app even when the legitimate one is already on the market, it does make the number of fake app downloads explode in a very short time.
To avoid this type of danger, Stefanko advises users to thoroughly check the app’s name and the developer’s name. “They must fit exactly, not only resemble what you expect,” he stresses.
The malicious apps have been since removed from Google Play.