14 bugs in Uber’s assets revealed sensitive info about drivers, riders
Researchers from consulting and technological audit outfit Integrity have discovered 14 bugs in a variety of Uber’s websites and mobile apps, most of which could reveal potentially sensitive information about drivers and riders.
As it turned out, six of these issues were already flagged by other bug hunters, but the rest were unknown to the company.
They shared some details about the vulnerabilities that have already been fixed by Uber.
One allowed brute-force attacks against the “promotion codes” feature in the payment page, permitting attackers to discover and use various codes:
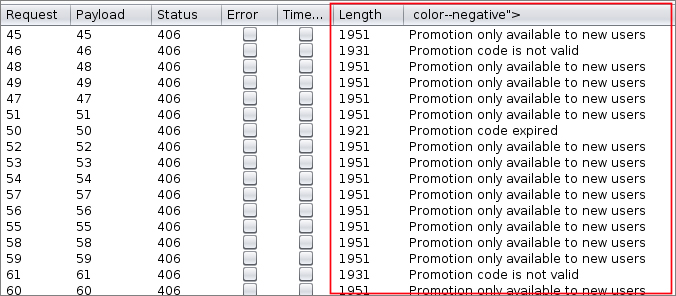
“Initially this issue was not considered valid because the promotions codes are supposed to be public and be given by anyone. This was true until finding an $100 ERH (Emergency Ride Home) code which they (uber-sec team) had no knowledge about. This ERH codes work differently from all others since even if a promotion code is already applied this ones can still be added,” they noted.
Others allowed researchers to discover users’ private email by using their UUIDs, enumerate UserIDs with phone numbers by taking advantage of a bug in the “split fare” option, view drivers’ waybill via their UUID (includes the driver name, license plate, last trip UUID, last passenger name, number of passengers, the origin and destination of the trip), and more.
“This was our first bug bounty program that we really dedicated some time, and we think it had a positive outcome. At the beginning we weren’t too confident with this program because a lot of people had already tested Uber in the private program, but after some time and when we started to find some good vulnerabilities it gave us the drive to continue and see where it could lead us,” the researchers noted.
“For the people who are starting the bug bounty programs, our advice is: never give up or be afraid if it is a big company, just have fun and try to learn as much as possible along the way and in time the profits will come.”
They did not reveal how much money they earned by discovering and reporting the flaws, but praised Uber’s security team for their efforts to fix as many of the flaws as soon as possible.
It appears that Uber did well by opening its bug bounty to the public.