How to block malicious macros for good?
Microsoft is finally doing something about the increasing threat of malicious macros: it has added a new feature in Office 2016 that will block macros from loading in certain scenarios.
“Recent data from our Office 365 Advanced Threat Protection service indicates 98% of Office-targeted threats use macros,” the company noted. “The enduring appeal for macro-based malware appears to rely on a victim’s likelihood to enable macros.”
With this new feature users will be unable to do so, no matter how convincing the attackers have made their lure.
The feature is controlled via Group Policy and can be configured per application, allowing enterprise administrators to block macros from running in Word, Excel and PowerPoint documents that come from the Internet (websites, file hosting services, file-sharing sites, documents attached to emails sent from outside the organization).
Block malicious macros
Administrators can enable this feature via each app’s Group Policy Administrative Templates for Office 2016.
The workflow goes like this:
1. Open the Group Policy Management Console, find the Group Policy Object you want to configure, right-click on it and choose Edit.
2. In the Group Policy Management Editor, go to User configuration.
3. Click through Administrative templates > Microsoft Word 2016 > Word options > Security > Trust Center.
4. Open the Block macros from running in Office files from the Internet setting to configure and enable it.
The feature will also hopefully provide teachable moments for the organization’s employees. The first warning upon opening a document carrying malicious macros will remind the user to be careful and to stay in Protected View mode (sandboxed environment).
If the user still proceeds to exit Protected View in order to access the content of the document, the new feature will block the execution of macros, and a new alert will tell him that, and perhaps teach him not to trust similar emails/documents in the future:
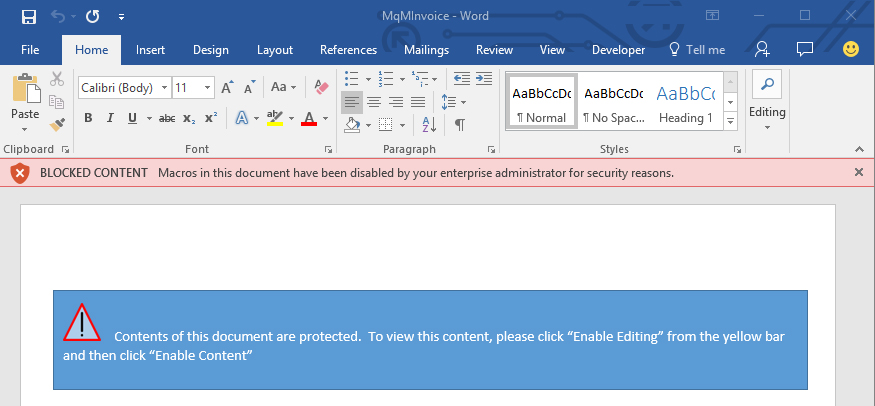
Of course, there are instances where macros included in documents aren’t malicious (they are legitimately used to load dynamic content into Office documents), so “users with legitimate scenarios that are impacted by this policy should work with their enterprise administrator to identify alternative workflows that ensure the file’s original location is considered trusted within the organization.”
Unfortunately, the new feature won’t mean much to non-enterprise end users, who are still stuck with the usual advice: don’t enable macros on documents you receive and aren’t completely sure are not malicious.