“Backstabbing” malware steals mobile backups via infected computers
In this day and age, our mobile devices carry more personal and business information than any other electronic device. Is it any wonder, then, that attackers want to have access to them?
But sometimes they can’t find a way in, and opt for the second-best option: stealing mobile backup files from the victims’ computer.
Palo Alto researchers dubbed the attack technique “BackStab”, and say it’s not new.
“While the technique is well-known, few are aware of the fact that malicious attackers and data collectors have been using malware to execute BackStab in attacks around the world for years,” they noted in a recently published whitepaper.
“Law enforcement of cials and jealous lovers around the world have used simple tools to capture and extract private phone information from computers to which they have gained access.”
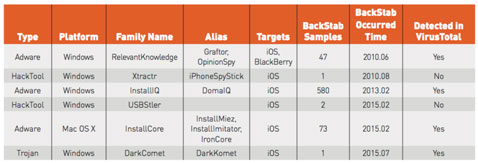
The researchers have identified 704 samples of six Trojan, adware and HackTool families for Windows or OS X systems that steal private user data from backup files of iOS and BlackBerry devices (click on the screenshot to enlarge it):
As it can be deduced from the table, iOS users were/are the most targeted. It’s also interesting that, for once, Android users are mostly safe from (these) attacks. “Unlike iOS and BlackBerry, there isn’t any desktop software developed by Google for Android device backup,” the researchers explained.
“The only official way to back up private data and application data from Android devices to a desktop computer is through the command line Android Debug Bridge (adb) utility included with the Android SDK. This is not a procedure commonly used by Android users, and the ADB backup le path and name are manually chosen by the user, making a successful attack of this kind much less likely.”
Of course, there are other way for Android backups to be stolen, but this particular technique is not effective enough.
For a BackStab attack to be effective, the malware or adware doesn’t have to have any special privileges on the infected computer, and the mobile devices from which the backups are extracted don’t have to be jailbroken or rooted.
Attackers can get the following information from unencrypted backups: call logs, messages (SMS and MMS), voice mail, contacts, email, calendars, noted, photos, audio and video recordings, web browsing history, cookies, geolocation history, documents saved on the device, device info, and more.
“The technique has been known to the security and forensic community for over seven years. There are many public articles and video tutorials describing how to conduct the attack using tools and/or open source projects available to the public,” the researchers pointed out. Two of the aforementioned six malware families have been capable of mounting this type of attack since at least five years ago.
iOS users can protect their data from this type of attacks by deleting all unencrypted iTunes backups they have on their computer, and by enabling encryption with a strong, unique password when they used the iTunes backup option. If they choose to backup into iCloud, a unique password and two-step verification for the iCloud account is the way to go.
Known malware families, such as DarkComet, can be blocked by AV solutions. Also, it’s a good idea to not click the “Trust” button when connecting the iOS device to an untrusted computer or charger via a USB cable.
“In some situations, official backup software, like that of iTunes, will automatically create backups of mobile devices without the user’s interaction and without encryption,” the researchers warned. “It is also possible for malware to initiate a backup when the device is attached to an infected computer in some cases.”