New technique makes phishing sites easier to create, more difficult to spot
Researchers have spotted a new technique used by phishers which could trick even more users into believing they are entering their information in a legitimate web form.
Instead of replicating as faithfully as possible a legitimate website – for example an e-commerce site – the attackers need only to set up a phishing page with a proxy program which will act as a relay to the legitimate site, and create a few fake pages for when users need to enter their personal and financial information.
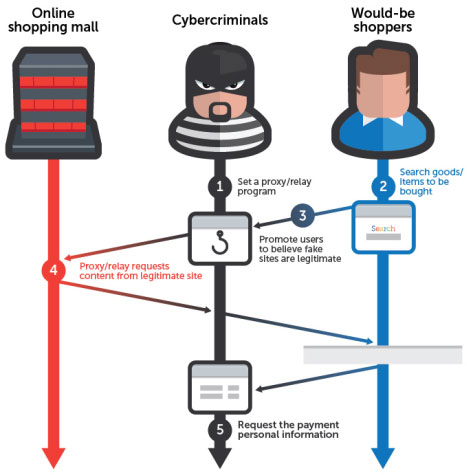
“So long as the would-be-victim is just browsing around the site, they see the same content as they would on the original site. It is only when any payment information is entered that modified pages are displayed to the user,” Trend Micro Senior Threat Researcher Noriaki Hayashi explains.
“It does not matter what device (PC/laptop/smartphone/tablet) or browser is used, as the attacker proxies all parts of the victim’s HTTP request and all parts of the legitimate server’s response.”
In the spotted attack, users are directed to the malicious site by clicking on a search result they got by entering a product’s name. The attackers used a number of blackhat SEO techniques to make the URL appear in the results. But spam emails and messages can also be used to lure potential victims to the malicious site.
The actual attack begins when the user clicks on the “Add to Basket” button on the legitimate site – the attacker has re-written the function so that the user is redirected to a spoofed e-cart page that leads to more fake pages simulating the checkout process.
The first page asks the victims to enter their personal information (name, address, phone number) as well as their email address and password. The second one requests the entry of credit card information (including the card’s security code). The third one asks for additional information that is sometimes required to authorize a transaction.
Once the victims have submitted all this information, they will receive a fake confirmation email for the purchase to the email address submitted – and the illusion is complete.
“So far, we have only identified this attack targeting one specific online store in Japan. However, if this attack becomes more prominent, it could become a very worrying development: this makes phishing harder to detect by end users, as the phishing sites will be nearly identical to the original sites,” Hayashi noted.
This approach makes phishing websites much easier to set up, and very difficult for the owners of the legitimate websites to detect.
Undoubtedly, we’ll be seeing more similar attacks in the future.