Detecting cyber attacks in a mobile and BYOD organization
 Mobile devices – laptops, tablets and smartphones – have been part of the information technology culture for some time. Enabling employees and contractors to bring their own devices to work has become a way of life for many organizations and may soon become the norm.
Mobile devices – laptops, tablets and smartphones – have been part of the information technology culture for some time. Enabling employees and contractors to bring their own devices to work has become a way of life for many organizations and may soon become the norm.
Many organizations understand that traditional perimeter security defenses are not effective at identifying attacks on mobile devices. This application note sets out to explore the challenges, understand the needs, evaluate mobile device management as an approach to detecting attacks and offer a flexible and high efficacy solution for detecting any phase of an ongoing attack on mobile devices regardless of device type, operating system or applications installed.
Personalization vs. security: Clashes in a changing culture
Over the past several years, organizations have begun adopting BYOD policies to create the kind of work environment that attracts and retains the best talent. The old days of standard-issue Windows PCs for new employees are over. College students no longer trek to the computer lab on campus and very often are choosing to use Windows PC alternatives such as MacBooks, Chromebooks, and iOS and Android tablets and smartphones for their scholastic and personal computing needs. Similarly, these alternatives are commonly the preference in high schools. These students-turned-new-employees frown at the idea of being told which device they must use at work and seek out employers whose computing culture aligns with their own.
A recent survey about BYOD and Mobile Security by the Information Security Group on LinkedIn (i) shows that the primary benefits of BYOD programs are improved employee mobility (57%), greater employee satisfaction (56%) and improved productivity (54%). The same survey indicates the biggest security concerns are loss of company or client data (67%), unauthorized access to company data and systems (57%) and user downloaded apps or content with embedded security exploits (47%).


This survey data demonstrates the challenge for IT organizations embracing BYOD. A BYOD policy increases productivity and satisfaction, but creates new critical risks that are hard to mitigate when directly controlling the device is no longer possible.
Data from the same survey indicates the strong momentum of BYOD implementation with BYOD is fully implemented by 31% of organizations and under evaluation by 20%. However, 21% of survey participants admit that personally owned devices are in wide use without official support of the organization (ii). This indicates that employees will find a way to use their own devices even when there isn’t a program in place.
No turning back
Regardless of the friction caused by this paradox between the freedom to personalize and the restrictions necessary for security, the trend is irreversible. A Gartner strategic planning assumption indicates “by 2020, 85% of organizations will adopt BYOD in some form.” (iii)

According to Gartner, enterprise device ownership will shift over a period of time. (iv)
This strategic planning assumption represents a big shift from 2013 where only 6% of organizations surveyed were completely BYOD.
Defeating your own perimeter
Many organizations’ security implementations focus on the concept of a defensive perimeter, which includes firewalls, intrusion prevention systems and sandboxes as well as endpoint security products such as antivirus software. BYOD and mobile devices including laptops, smartphones and tablets defeat the goal of perimeter security, which is to block an attack at the entry to the organization. Employees, contractors and customers use these devices inside and outside the perimeter. If their devices are infected with malware outside the perimeter, the malware will be physically carried into the network past all the network perimeter defenses.
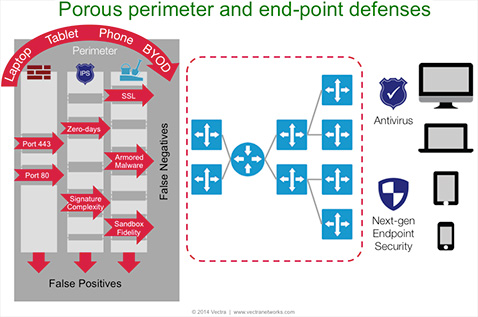
Malware on mobile devices circumvent perimeter defenses leaving the network exposed as BYOD become the norm.
Perimeter defenses look for malicious traffic coming into the organization from the outside rather than assuming that the malware is already inside and they are generally ineffective at protecting against this attack vector. For devices owned by employees, the IT department is often unable to require installation of endpoint security software, leaving this traditional security approach ineffective as well. As BYOD use increases, so does the lack of visibility and control over security.
Malware: It’s not just for laptops anymore
Laptops are still the primary mobile devices used to physically carry malware into an organization. The detections graph below reinforces the reality that mobile laptops – regardless of their owner – are one of the largest sources of malware in an organization.
Detections report for a Vectra X-series Platform in a production network.
Note the orange line dropping from 35 command and control detections on Friday April 18 to less than 5 on Saturday, April 19, then rising back to nearly 30 on Monday April 21. This happened because employees closed their laptops and took them home for the weekend. In this real customer example, over 85% of the command and control detections were for laptops.
Tablets and smartphones will quickly catch up to laptops for malware infections in organizations. Gartner published a strategic planning assumption that “by 2017, the focus of endpoint breaches will shift to tablets and smartphones.” (v)
The trend is already visible. The first Android botnet was reported in June 2012 and the first Android botnet using The Onion Router (TOR) in February 2014. This TOR-enabled botnet can be rented for $500 per month plus a $1,000 one-time setup fee. In March 2014, WinSpy RAT became available for Windows and Android mobile devices. In July 2012, a grey-hat company called Hacking Team released the Da Vinci Remote Control Suite to Government organizations, enabling them to intercept content on Android, Windows and iOS mobile devices regardless of encryption, transparent to the user and with no discernible impact on battery life.
A collection of nearly 12,000 Androids app files from third-party sites (other than Google Play) were scanned using Metascan Online and nearly a third, or over 3,500 files, were flagged as having a potential threat by one of 40 malware engines. Two or more malware engines flagged 919 of the 12,000 app files, which is 26% of the samples likely containing malicious software.

74 percent of the app files were flagged by a single malware engine. The remaining 26 percent flagged represent 8 percent of the nearly 12,000 app files scanned.
Similarly, Cisco reports that 97 percent of all mobile malware in 2013 targeted Android devices, while Android users also had the highest encounter rate (71 percent) with all forms of web-delivered malware. (vii)
Plugging the gap with Mobility Device Management solutions
To keep pace with both the employee expectations for BYOD and mobility and the organizations’ requirements for security, IT departments have been deploying mobile device management (MDM) solutions. MDM is often the preferred BYOD solution that requires employees to allow installation of security client software on their personal devices. This gets tricky when the devices aren’t actually company-owned.
However, MDM software doesn’t actually detect the presence of malware on a laptop, tablet or smartphone. MDM provisions and manages devices to ensure an employee-owned device inherits the user’s enterprise persona, thus centralizing authorization for email access and blocking network access to jailbroken devices since they represent a significant vulnerability. MDM solutions can also attempt to manage access and use of applications from branded and third-party app stores as well as preventing a device from incurring international plan surcharges.
According to Gartner, “by 2016, 20 percent of enterprise BYOD programs will fail due to enterprise deployment of MDM measures that are too restrictive.” (viii) This will occur if IT departments implement MDM with a similar level of control over employee-owned devices that they had on company-owned personal computers. At the same time, employees are increasingly aware that MDM provides IT organizations access to their personal information, such as personal email, photos and social media posts. Employees are demanding solutions that isolate personal content from business content and restrict the ability of the IT organization to access or change personal content and applications.
Real-time threat detection for BYOD & Mmobility security
According to Gartner, enterprises are overly dependent on blocking and prevention mechanisms that are decreasingly effective against advanced attacks. (ix) Existing blocking and prevention capabilities are insufficient to protect against motivated, advanced attackers, but most organizations continue to be overly invested in prevention-only strategies. Information security doesn’t have the continuous visibility it needs to detect advanced attacks when computers are company-owned and BYOD exacerbates the problem further.
What’s needed is a solution that finds threats that evade and circumvent the limited protection that perimeter-based defensive technologies provide against motivated, advanced attackers.
Some vendors are implementing real-time threat detection capabilities that can sit deep inside the network to detect when an attack has evaded perimeter defenses while it is happening. These products simply listen in passive mode on your network and use data science and machine learning to understand what is normal, or white behavior, so they can detect anomalous behavior.
Advances in data science and compute power enable machine learning to work for much higher bandwidth network connections than just a few short years ago and produce results in near real time. As a result, these new real-time threat detection platforms can listen to the internal network traffic and spot multiple phases of an attack and provide multiple opportunities to stop a targeted attack before data is lost.
This approach is different from a perimeter defense system like a firewall, intrusion prevention system or sandbox that typically only detect the initial exploit coming into an organization. Another benefit is real-time detection uses no agent software and can work for any device, any operating system and any application since it only needs to apply machine learning to the network traffic. As a result, real-time threat detection complements perimeter security and provides significant depth of detection.
In the diagram below, the perimeter security would detect the initial exploit, but the real-time detection platform could detect command and control communications of either opportunistic or targeted attacks as well as all phases of an ongoing targeted attack.
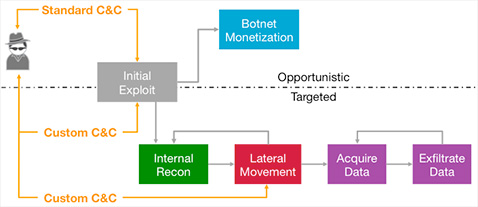
Real-time Detection Platforms can detect any phase of an ongoing opportunistic or targeted cyber attack.
In five-years time, real-time detection platforms may be the foundation for network security to meet the ever-increasing growth of BYOD and mobile.
References
i “2014 BYOD & Mobile Security Survey,” LinkedIn Information Security Group
ii “2014 BYOD & Mobile Security Survey,” LinkedIn Information Security Group
iii “Defining BYOD Ownership and Support Expectations in Contracts Ensures Successful Implementation,” by DD Mishra and David Edward Ackerman, April 25, 2014, ID G00261616.
iv “Defining BYOD Ownership and Support Expectations in Contracts Ensures Successful Implementation,” by DD Mishra and David Edward Ackerman, April 25, 2014, ID G00261616.
v “Predicts 2014: Mobile Security Won’t Just Be About the Device,” by Ray Wagner, Dionisio Zumerle, John Girard, Joseph Feiman, November 22, 2013, ID G00258488.
vi OPSWAT study April 14, 2014, http://www.opswat.com/blog/scanning-malware-android-applications
vii 2014 Annual Cisco Security Report.
viii “Predicts 2014: Mobile and Wireless,” by Ken Delaney, November 8, 2013, ID G00255829.
ix “Designing an Adaptive Security Architecture for Protection From Advanced Attacks,” by Neil MacDonald and Peter Firstbrook, 12 February 2014, ID G00259490.
