Banking malware sniffs out data sent over HTTPS
Careful online banking users can sometimes spot that something is amiss when malware installed on their computer pops up phishing pages or adds fields to legitimate banking forms. But the Emotet banking malware doesn’t bother with that, and sniffs out data sent over secured connections instead.
According to Trend Micro researchers, German users are particularly in danger from this malware family, although infections have also been spotted in the rest of the EMEA region, as well as in North America and the Asian-Pacific region.
The variants targeting German users are delivered to the victims via fake bank transfer notifications and shipping invoices. Clicking on the embedded links triggers the download of the malware.
The first thing that the malware then does when run is contact its C&C, from which it downloads additional files, including the configuration file that contains information about targeted banks.
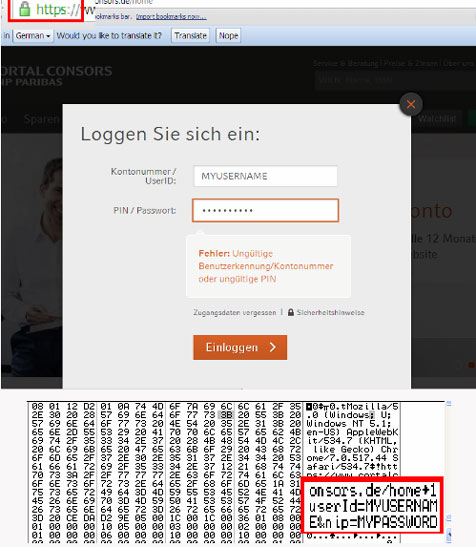
“Another downloaded file is a .DLL file that is also injected to all processes and is responsible for intercepting and logging outgoing network traffic. When injected to a browser, this malicious DLL compares the accessed site with the strings contained in the previously downloaded configuration file,” the researchers explained.
“If strings match, the malware assembles the information by getting the URL accessed and the data sent. The malware saves the whole content of the website, meaning that any data can be stolen and saved.”
The malware is also capable of hooking into a number of network APIs, which allow it to sniff out data sent over HTTPS:
Emotet uses registry entries to store the stolen (and encrypted) information, likely in an attempt to hide its activity from users and AV solutions.