Backdoor Trojan uses “magic code” to contact C&C server
Researchers from security firm Seculert have unearthed a curious piece of backdoor-opening malware.
Once the malware gets installed on a computer and run, it first contacts the server via the HTTP protocol. After that first time, the C&C server instructs it to start communicating with the same IP address and port, but to use a custom-made protocol and to start every communication with (literally) “some magic code”:
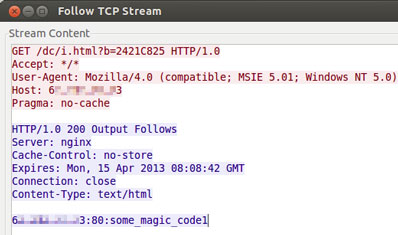
The malware is instructed to create a backdoor account, giving the attackers permanent access to the machine. Still, they currently don’t seem to misuse it.
“As the malware is capable of setting up a backdoor, stealing information, and injecting HTML into the browser, we believe that the current phase of the attack is to monitor the activities of their targeted entities,” Seculert’s Aviv Raff pointed out, adding that the fact that the malware is capable of downloading and executing additional malicious files might indicate that this is just the first phase of a much broader attack.
It’s also interesting to note that the malware sample they first detected has been on the infected computer for nearly a year, and that most (78 percent) of the several thousands of different entities that they discovered having been targeted since are overwhelmingly located in the UK.