Is a German criminal behind the latest ransomware campaign?
Ransomware distribution campaigns are coming fast one after the other and its usually difficult – if not downright impossible – to discover anything about the criminals behind them.
But Roman Hussy, the well-know security activist behind the Zeus, SpyEye and Palevo Trackers, has recently discovered a new campaign that seems to point towards a German-speaking criminal that did his homework well.
The campaign itself is pretty standard: users are redirected to websites hosting the BlackHole exploit kit, which takes advantage of a browser or plugin vulnerability to install a piece of ransomware on their computers.
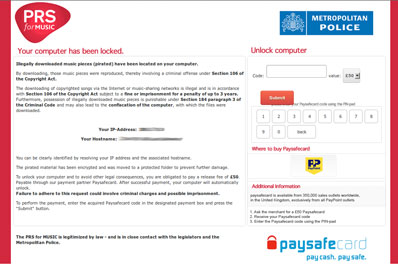
The malware then contacts its C&C server, which geolocates the infected computer and redirects it to a page with the warning message in the appropriate language and supposedly coming from the local police and an organization that collects royalties in the user’s country (click on the screenshot to enlarge it):
According to Hussy, Swiss, German, Austrian, French, Dutch and British users are all being targeted simultaneously, and in addition to the ransomware, they also get saddled with the Aldi Bot Trojan which, among other things, steals passwords and banking credentials.
What Hussy discovered when he investigated the C&C server in question (located at joonwalker.com) is that judging by the URLs for each specific ransomware note, the criminal behind this campaign is a German-speaking individual.
He also points out that the criminal has obviously spent quite some time in preparing each message, as there are very few grammatical and spelling errors. The information about where the users can buy Paysafecards in their own countries is correct, he points out, and the same can be said about the the names of the associations that track copyright infringement in each country.
He also tracked the registration information for the C&C domain, which was supposedly registered by one Huth Matthias from Gladbeck, Germany.
While that information is probably false, it is good to know that over 60 other domains were registered with that same information this year, and they should be considered malicious and be blocked on the networks’ edge. For a complete list, go here.