This is how Windows get infected with malware
When a Microsoft Windows machine gets infected by viruses/malware it does so mainly because users forget to update the Java JRE, Adobe Reader/Acrobat and Adobe Flash. This is revealed by a survey conducted by CSIS Security Group A/S.
Basis of the study
CSIS has over a period of almost three months actively collected real time data from various so-called exploit kits. An exploit kit is a commercial hacker toolbox that is actively exploited by computer criminals who take advantage of vulnerabilities in popular software. Up to 85 % of all virus infections occur as a result of drive-by attacks automated via commercial exploit kits.
The purpose of this study is to reveal precisely how Microsoft Windows machines are infected with malware and which browsers, versions of Windows and third party software that are at risk.
We have monitored more than 50 different exploit kits on 44 unique servers / IP addresses. Our figures come from the underlying statistical modules, thereby ensuring an as precise overview of the threat landscape as possible.
The statistical material covers all in all more than half a million user exposures out of which as many as 31.3 % were infected with the virus/malware due to missing security updates.
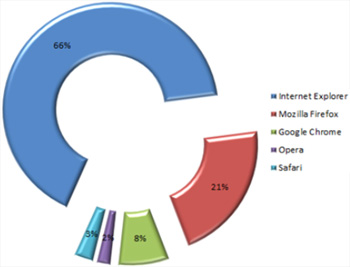
The thousands of users who unknowingly have been exposed to drive-by attacks have used the following web browsers:
Illustrated below is users distributed by the operating system that has been exposed to malicious code:

The numbers of Danish users who have been exposed during the observed period represent a total of 13,210 of which 2877 have been force-fed with malicious code – probably without the users’ knowledge. More than 80 % of the total number of infections is a so-called cocktail of viruses/malware, which typically consists of information and data thieves and fake security programs.
Most vulnerable programs
On the basis of the total statistical data of this study it is documented that following products frequently are abused by malware in order to infect Windows machines: Java JRE, Adobe Reader / Acrobat, Adobe Flash and Microsoft Internet Explorer. A more detailed summary is given below:

Vulnerabilities abused
Among the vulnerabilities we have observed abused by the monitored exploit kits, we find:
CVE-2010-1885 Microsoft Help & Support HCP
CVE-2010-1423 Java Deployment Toolkit insufficient argument validation
CVE-2010-0886 Java Unspecified vulnerability in the Java Deployment Toolkit component in Oracle Java SE
CVE-2010-0842 Java JRE MixerSequencer Invalid Array Index Remote Code Execution Vulnerability
CVE-2010-0840 Java trusted Methods Chaining Remote Code Execution Vulnerability
CVE-2009-1671 Java buffer overflows in the Deployment Toolkit ActiveX control in deploytk.dll
CVE-2009-0927 Adobe Reader Collab GetIcon
CVE-2008-2992 Adobe Reader util.printf
CVE-2008-0655 Adobe Reader CollectEmailInfo
CVE-2006-0003 IE MDAC
CVE-2006-4704 Microsoft Visual Studio 2005 WMI Object Broker Remote Code Execution Vulnerability
CVE-2004-0549 ShowModalDialog method and modifying the location to execute code
The reason why patching are essential
The conclusion of this study is that as much as 99.8 % of all virus/malware infections caused by commercial exploit kits are a direct result of the lack of updating five specific software packages.
An effective solution
With this study CSIS has received confirmation that our security program Heimdal is addressing a market not adequately covered by a proper patch routine or policy for this area. Since the statistical figures cover both private PCs and machines used for business purposes, it is our opinion that this is a general problem.
Heimdal can be used in several versions: a free test version, a pro version with advanced functionalities such as web filtering securing your online presence, and finally a corporate version which can easily be distributed and administered in a Microsoft Windows network.

Author: Peter Kruse, Partner & Security Specialist at CSIS.