SpyEye-fueled man-in-the-mobile attack targets bank customers
The customers of a European bank have recently been targeted by a man-in-the-mobile attack featuring a SpyEye variant.
“The bank uses SMS based mTANs to authorize transfers,” explain F-Secure researchers. “The trojan injects fields into the bank’s webpage and asks the customer to input his mobile phone number and the IMEI of the phone. The bank customer is then told the information is needed so a ‘certificate’ can be sent to the phone and is informed that it can take up to three days before the certificate is ready.”
The “certificate” – actually a Trojan – contains various files, among which is the malicious sms.exe and a second installer that contains another executable whose sole task is to display the following message on the user’s phone:
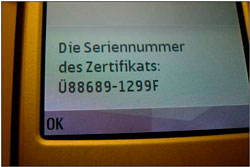
The message serves only to reassure and convince the user that the Trojan is actually the promised certificate and to prevent him from becoming suspicious.
“The trojan is signed with a developer certificate. Developer certificates are tied to certain IMEIs and can only be installed to phones that have an IMEI that is listed in the certificate. This is why the malware author(s) request the IMEI in addition to the phone number on the bank’s website,” explain the researchers. “Once they receive new IMEIs, they request an updated certificate with IMEIs for all victims and create a new installer signed with the updated certificate.”