Acunetix Web Vulnerability Scanner 4.0
Ten years ago I started working for a small San Francisco based startup that was offering consulting services for financial institutions. One of my first duties there was to be a part of a small penetration testing team. Back then we had some good pieces of code that was helping us to test clients modem connections, file servers and different networking equipment.
At my current job position, my employer often sends me to information security conferences all over the States. From the lectures I attend and companies exhibiting, it is very obvious that the current hot trend is web application security. With a growing number of businesses going online, web applications became one of the biggest security issues. The types of scanners we used back then evolved to another level following the latest threats.
Acunetix Web Vulnerability Scanner is one of the rather new products in the evolving web application security market. Before I start this review, I must give you a disclaimer – because of company policy, some of the screenshots accompanying the review will be obfuscated or even taken from a scan of Acunetix test web servers.
For the purpose of this review I used the latest version of Acunetix Web Vulnerability Scanner available – 4.0. With an installation file of just above 8 MB, the software will take approximately 25 MB of space. A straightforward software GUI offers an optimized three-column structure. From left to right we have a main set of options and tools, scan results and a window containing details of a selected vulnerability alert. The bottom of the screen hosts a real time activity window that shows the progress of the scanning process.
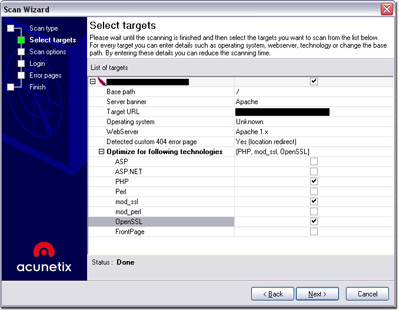
There are four different scan types. The default one offers a normal procedure where one web site gets all the attention. If the user wants to scan multiple sites, there is an option to select a file that contains the list of URls. If you already used the software’s built-in crawler module, you can also act upon its results. The final scan type offers scanning of a range of IP addresses with web servers running on ports specified by the user. I mostly used the default option for scanning a single web site. After chosing this option, user is able to use predefined set of scanning profiles and to set specific crawling options. If in any case the target web server is located behind a HTTP authentication window, you will be able to fill in your credentials. When you setup the initial scan settings, hitting the finish button will fire away the scanner.
Although the automatic scan finds a huge amount of specific information that could result in a possibly vulnerable application, the “Manual browsing window” that opens during the scan is surely a nice touch by the developers. In the window, the user can browse the site that is being scanned so the software crawler can identify the files that are not directly accessible or were not discovered by the crawling process. This option is especially interesting with web sites that use JavaScript navigation.
Time consumption is an important aspect of vulnerability scanners. Both on a simple PHP based blog, as well as a large multi-user web application, Acunetix Web Vulnerability Scanner was a bit slow. Because of connection differences, there is no point of mentioning specific timeframes in which the software was able to scan the systems, but the performance is directly connected to the complexity of the tests. I have set it up to check all the possible details on both scanning scenarios, so I expected a longer scanning period.
Acunetix Web Vulnerability Scanner offers its users real time reporting. For instance, when the software was in the middle of lenghty scan of a complex PHP web application scenario, I was able to check the issues that were already discovered. Alert breakdown is done with four colors, each of the representing attack severity – red (high), orange (medium), blue (low) and green (information).
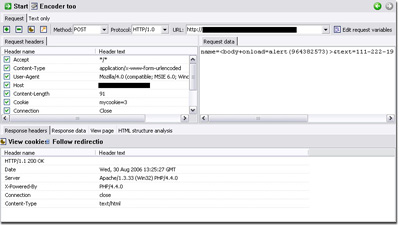
The alerts are presented to the user in an easy to manage format: vulnerability type -> vulnerability item -> description. Under the vulnerability description, the most interesting thing is to check out attack details. For every detected vulnerability, the user can see the actual HTTP headers that triggered the vulnerability as well as the HTML response given by the tested server. Besides this, the software uses an innovative approach allowing the user to modify and replicate the same attack via a built-in HTTP Editor module. Within this GUI, users can craft specially structured attacks and analyze the server response.
There is a slight bug with the attack launching that manifests in vulnerability items that are clearly not exploitable. For instance, inside a blue alert that says “Broken link”, the user can try to launch this attack. There is obviously no attack related to this, but the software AI doesn’t understand the difference. I didn’t come across any other buggy issues with the software, so I thought about mentioning this one.
Advanced users will find the “Vulnerability Editor” option very interesting. There you can list and edit all the vulnerability types and specific items that Acunetix uses for scanning. I was really satisfied with the way how users can create new items by cloning existing vulnerability information. On this way, users develop custom sets of vulnerability scanning actions that would be optimized for their servers, as well as manually update sections of the current vulnerabilities.
Besides HTTP Editor, Acunetix Web Vulnerability Scanner offers a couple of other invaluable tools. With HTTP Sniffer users can create a custom set of traps that would be recorded in the sniffing period. By the way, by enabling the sniffing option, the software starts a proxy on port 8080. HTTP Fuzzer is a nice addition that is used for crafting specific requests and tracking the server’s response. The option is especially worthy when used with one of the predefined number/character generators which append their output to the requests. The last tool I actively used inside Acunetix WVS is an Authentication Tester, a brute force module that can be configured for testing both HTTP and HTML form authentication methods.
The bottom line is that Acunetix Web Vulnerability Scanner 4 is a powerful and versatile scanner that proves to be an important piece of a web application-testing arsenal. As always with penetration testing, some things must be done manually, but from the perspective of an automated web vulnerability scanning procedure, you cannot miss with Acunetix WVS.