SonicWALL Pro
In my day job, I work as the technology director for a small, rural high school in the United States. When the school finally installed its first labs and a T1 connection several years ago, the firewall and filter solution recommended by most schools in the area was the SonicWALL Pro.
SonicWALL’s line of firewalling appliances are recommended for small- to medium-sized networks in various environments. Their ease of setup and configuration make them ideal for novice users to install when dedicated support staff is not available. The appliance further offers filtering capabilities to prevent students and/or staff from surfing where they don’t belong, and the more advanced models also provide VPN and antivirus capabilities.
As a user of a SonicWALL product for the past four years, I thought I would go ahead and share my experiences.
Setup & Configuration
The model in use at our school is the SonicWALL Pro, a rack-mountable version with unlimited user access that has since been replaced by newer models. However, the functions and features of newer models are very similar, if not identical, to the firmware in place on this model.
The Pro has three ports labeled LAN, DMZ, and WAN, and firewall rules make reference to these ports, making setup quite easy. After initial installation, the administrator merely points a browser at the default IP address, enters their own IP and route information, and registers (required for firmware updates and such). The box is up and running in a matter of minutes.

The login screen is shown in Figure 1. Ours is set to be managed through Internet Explorer, which works flawlessly with the SonicWALL interface. Opera 6.5 will connect, but there appears to be some difficulty with passing the password on to the firewall as it only reloads the initial login screen and never into the config menus. Earlier versions of Konqueror (pre KDE 3.0) also failed to work properly. There are, fortunately, other ways to manage the SonicWALL (covered below).
The user name Admin is used for all management functions, and unfortunately the account is not editable. Additional users may be added, but only to bypass firewall rules and filters. When Admin logs in, the user is presented with the last menu they visited before logging out. Other users are given a simple message stating they have access to privileged services. These privileges time out after a time specified by the administrator, so there is no need for the user to log off.
Figure 2 is a screenshot of the General menu. The Status tab (shown) shows the basic configuration options at a glance as well as some information about the hardware. The Update Firmware Now button makes it easy to download upgrades, but I’ll get to why I haven’t done that in a moment. The remaining tabs are for entering network information (IP, Subnet, DNS, NAT, etc.), setting the time (capable of pulling from a NTP server), and changing the admin password. Note that Admin access can be granted from the LAN interface only, so external users will not be able to connect and alter settings, particularly useful for a site using weak passwords or susceptible to social engineering.
Features
Moving down the line of options on the left-hand menu bar, we next come to Logging. This speaks for itself, and it will log just about everything a user could want, from logins (failed and successful) to dropped/refused network connections to attempted attacks and more. The box will email logs and alerts to an administrator if desired, and logging can be set to either overwrite logs or shut the system down when full, depending on the user’s needs.
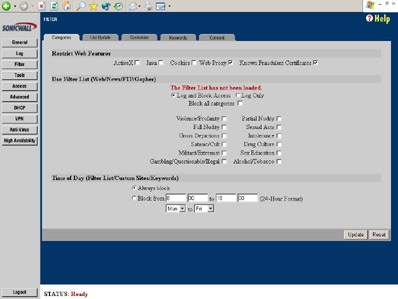
Next we have the Filter menu, shown in Figure 3. The box comes with a one-year subscription to SonicWALL filtering lists, but subsequent years will cost money (upwards of $800 for a school our size). Fortunately the filter can be completely customized without a subscription. I roll my own because of both the expense and the overly-paranoid lists provided by SonicWALL.
As seen in the filter menu, the box can block the given features (though we find this causes too many problems). If a user surfs to a blocked site, they are redirected to a simple page stored on the box that displays the SonicWALL logo and a simple, configurable message from the administrator (Figure 4). Should administration choose only to filter traffic at certain times, say only during school or work hours, that option is available.
I would like to note here that the blocking is less than perfect in terms of enforcement. The box reads all plain text passing through port 80, so surfing to a blocked site’s IP address will still result in access. Thus, a creative student or employee familiar with DNS will be able to find their way to blocked domains. Similarly, surfing through a proxy/anonymizer will bypass the filtering rules when web proxies are not blocked. This forces administrators to be more creative with the use of keywords. In addition to URLs, filtering is enforced on web searches, web-based email, and message board and blog posts, because, again, this information is passed in plain text through the filter.
The Customize tab allows the user to set up trusted domains (where no filter enforcement takes place) and to block domains not specified by SonicWALL’s lists. Users should also be careful with the Keywords tab. We once blocked the word “sex”, but soon discovered not only does this cause problems with gender-related sites but location names, such as a town named Essex. Another issue is blocking “xxx”, which may appear in randomly-generated URLs or searches for things like Super Bowl XXXV. The last tab is Consent, where users have time limits to visit pages, but this is not something we have any use for.
Of course, these shortcomings are not specific to SonicWALL; filters from just about all sources have this problem to some extent. I only mention it because it would be too easy for an overzealous or paranoid administrator to enter any number of keywords that are only objectionable in certain contexts, resulting in all sorts of headaches.
The Tools tab is simple. Here the firewall can be restarted, settings and config files can be backed up (they are saved as text files on the user’s hard drive or on a networked drive), upgrade keys can be entered, and simple utilities like ping, traceroute, and DNS lookup are available. The user can also generate a troubleshooting page that can be sent to SonicWALL for technical support.
Next we have the Access menu, shown in Figure 5. This is the firewall. As you can see, the basic Services tab is easy to use; various services can be allowed or denied going out of the LAN or in to the DMZ with a simple checkbox. A stealth mode can be activated where the firewall will silently drop all connections directed to the LAN. In the Add Service tab, almost every port is listed by name, and custom ports and protocols can be added.
The Rules tab is where the real action takes place. This is more akin to standard firewall rulesets and is initially generated based on entries in the Services tab. The Rules tab allows finer control for knowledgeable administrators, however, and can be customized down to specific IP addresses or ranges, the direction (LAN to WAN, WAN to DMZ, etc.), default behaviors, and so forth. All traffic is applied down the chain in order of the rules, and while the order of the rules cannot be manipulated directly, the box is smart enough to place rules such as Default Deny at the bottom of the chain.
Users and management options are included on the Access menu. SNMP management is available, as is management by the “SonicWALL Global Management System”, but I have tried neither of these options. I believe attack signatures (NetBus, Sub7, etc.) are included in firmware upgrades and are part of the firewall component, as nowhere are there options to enable/disable filtering based on known attacks.
The Advanced tab allows for creation of network routes and customizing NAT addressing and things like Ethernet speeds, but most users will not have to touch these settings.
The DHCP tab allows users to establish the box as a DHCP server should they choose not to use a server or if they do not have one available. Ranges and static addresses may be established as well, and options include the default gateway and DNS and WINS server addresses. Incidentally, the box can also accept DHCP configuration for the WAN port from cable modems and other broadband connections.
VPN is available on this model, though I have not had an opportunity or need to play with it yet. If I ever get around to it, I will provide a separate review in the future. In poking around, however, I see there are a handful of encryption algorithms and so forth available. My understanding is most VPN clients will be able to connect to the box without difficulty.
Finally, the box offers Anti-Virus and High Availability options, but I have not paid to upgrade to these services and cannot provide an evaluation.
Final Thoughts
In all, I’ve been very happy with the capabilities of the SonicWALL product. Its filtering, even without subscribing to SonicWALL’s lists, is adequate for our purposes and still allows our school to meet the requirements of the Children’s Internet Protection Act in the U.S. Students still slip by from time to time, but again, this is inevitable and our school believes filtering should not be a substitute for teacher supervision anyway.
The only problem I have had with SonicWALL is support. Following a firmware upgrade in mid-2002, we had problems with the box refusing to pass traffic. It seemed to occur at random, and the only way to restore connectivity was to power cycle the box. Getting tech support requires visiting SonicWALL’s website, logging in, and posting a message as if to an online forum. I uploaded the tech support reports generated by the box and spent several days posting and replying to messages but had no luck. Ultimately I restored the earlier firmware from backup and I was back in business.
Some time later, SonicWALL announced a flaw in the new firmware that resulted in loss of connectivity if filtering was enabled. I find it hard to believe a problem of this magnitude could make it through testing, but it certainly explained our problems. As a result I’ve been hesitant to download new firmware updates and I typically wait a couple weeks and talk to the handful of other schools in our area who are also using SonicWALL products.
Despite this, I would still recommend SonicWALL’s products for smaller environments and for institutions who cannot afford a full-time network technician. They are easy to install, easy to maintain, and generally very reliable. More advanced users, however, could easily set up similar solutions for a fraction of the price, especially using Open Source products.