Review: Group-IB Digital Risk Protection
The COVID-19 pandemic has transformed our private and working lives. It has also forced companies to extend the network perimeter due to employees working from their homes and to accelerate digital transformation efforts across the board. The latter push resulted in the hurried adoption of new systems and services outside of the enterprise, requiring serious efforts and in-depth technological knowledge to protect these new attack surfaces.
Digital transformation also changes the game of online presence. For example, if you are selling physical products, you can’t afford to dismiss digital channels anymore. Ten to fifteen years ago, having an online presence meant having a web page with your phone number and email address, maybe a rudimental web shop. Today, digital transformation opened new channels – such as social networks (Facebook, Twitter, Instagram, LinkedIn, etc.) or e-commerce platforms (Amazon, eBay, AliExpress) – that enable companies to directly engage with customers.
These digital channels are used by companies to boost their digital reputation by using their own assets (logo, branding, and marketing strategy) and customer’s activities (e.g., quality feedback about the product or service). The problem is, though, that the internet was never intended to be a safe place and it’s difficult to predict how it will be misused. Logos, content, offers, and partnerships can be misused by criminals to “make” money. Companies must take proactive measures to defend their brand and reputation and minimize / eliminate this digital risk.
Here are some examples of malicious actions that can increase a company’s digital risks:
- Scammers using its brand to promise fast profit and/or selling counterfeit goods with its brand
- Reputational leaks
- Fake partnership advertisements with the company logo
- Brand misuse in phishing attacks
In other words, these threats exist outside your network perimeter and can be devastating in terms of public relations and brand damage.
The number of scammers is growing daily, and the need for new tools and techniques to combat them grows. Also, the internet is larger than its immediately visible part, and organizations should be aware that fraudulent activities affecting their reputation are also common on the dark web and hidden services.
In this review, we will analyze Group-IB Digital Risk Protection, an Al-driven product that helps detect the exposure of your digital assets and protect them from misuse.
Digital Risk Protection
Group-IB Digital Risk Protection (DRP) is a tool that helps companies protect their intellectual property at all levels – internally, on the indexed web, but also in the dark web (sites with the “.onion” domain, accessible via specialized software). This is done by monitoring the entire online space for brand mentions and using machine learning algorithms to prioritize threats and actions.
The onboarding process for Group-IB DRP starts with defining the company’s digital assets that must be protected. This step is managed with the support of the DRP Customer Success team, which guides users through the process of registering their company and assessing and defining the digital footprint they want to protect. Clients will also soon be able to configure all those settings themselves, but assistance for tuning and configuring Group-IB DRP properly will still be provided (if needed).
For reviewing purposes, we went through the prototypical onboarding process and monitored popular Facebook brands – Instagram, WhatsApp, and Messenger – because they often suffer copyright infringement and other violations and are frequently misused by scammers.

Figure 1 – We monitored popular Facebook brands (Instagram, WhatsApp, and Facebook Messenger)
After the registration and onboarding, users can start monitoring their organization’s digital footprint or can choose a license type where the monitoring is performed by Group-IB analysts.
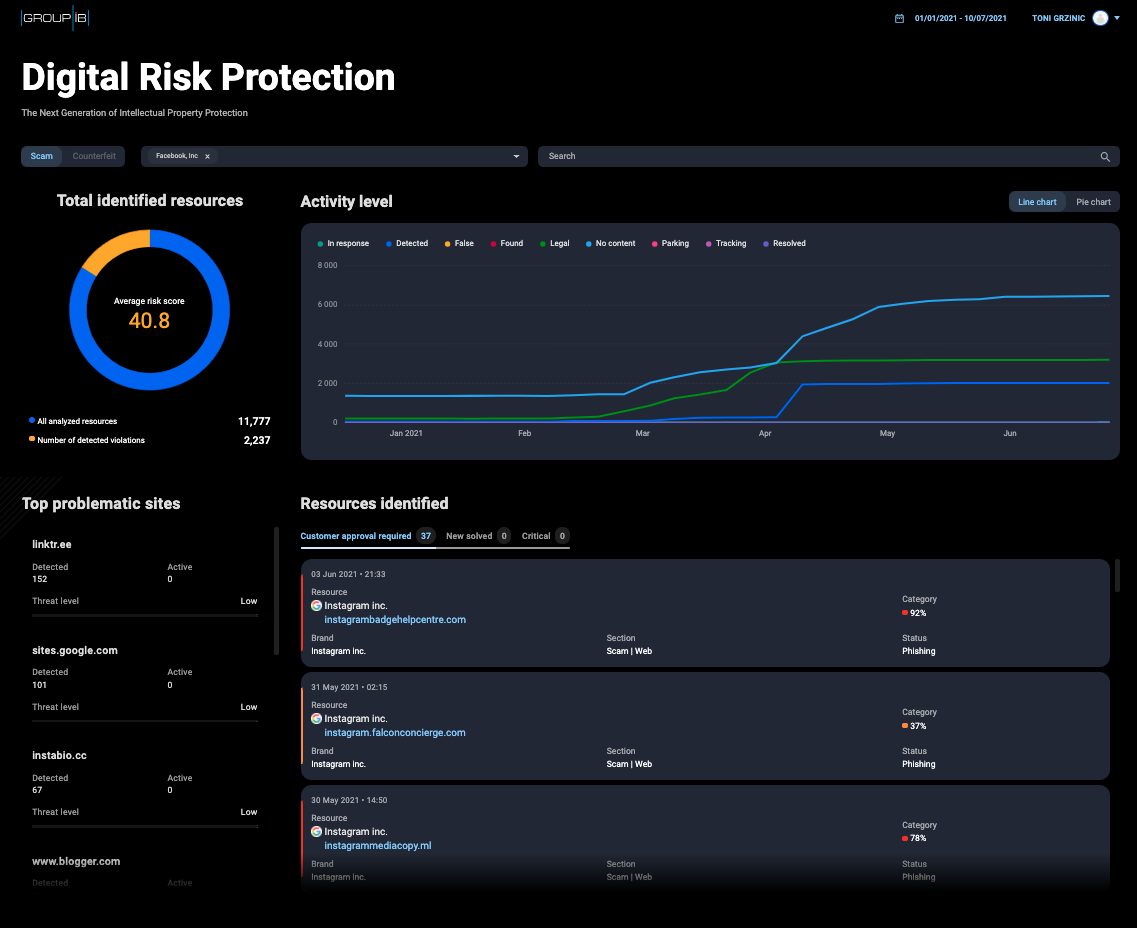
When users log into Group-IB DRP they are presented with a clear dashboard that contains the overall risk level of their company and events that need attention (Figure 1). If they are monitoring multiple companies or brands, they can filter the results in the dashboard.
Figure 2 – Group-IB Digital Risk Protection (DRP) dashboard
Based on their brand profile, Group-IB DRP scrapes and analyzes the web and tracks the company’s digital presence. It monitors the following sources constantly:
- Domain names and their reputation
- Websites
- Social media
- Mobile application stores (official and non-official)
- Marketplaces, online ads, and classifieds
- Instant messaging platforms
- The deep and the dark web
Group-IB DRP collects and analyzes more than 3 million events daily. The monitoring phase provides the organization with early alerts about brand mentions and, based on the content, assigns a risk score based on the type and priority of misuse. Group-IB DRP helps users prioritize how to approach and work on a specific incident, and also to decide when to include Group-IB analysts to help assess the most difficult cases.
The main goal of Group-IB DRP is to prevent data, revenue, and reputational losses. The platform has five main modules to prevent common threats to a company’s digital presence:
- Anti-Scam: Protection against online abuse taking usual forms like scams and phishing, fake partnerships and trademark abuse, fake advertisements, fake accounts, brand impersonation on social media, and fake mobile apps (Figure 3)
- Anti-Counterfeit: Protection and detection of illegal sale of goods or counterfeited versions, cases of copyright infringement, breach of partnership agreements (Figure 4)
- Anti-Piracy: Protection against illegal distribution of digital content in all forms (video, audio, software, computer games, streaming services, books, articles, etc.), monitoring torrent trackers, streaming services, or pirated platforms on social media and the dark web. The pirated content is, on average, detected under 30 minutes, and most illegal copies are fully blocked in under 7 days
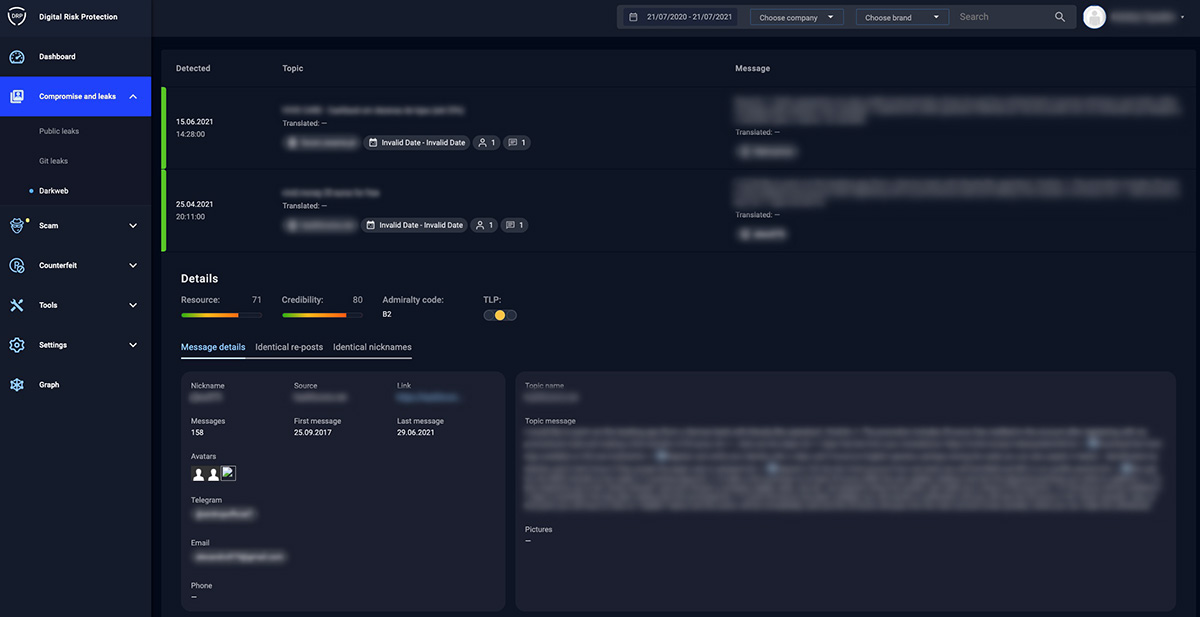
- Leak Detection: Detection of sensitive data exposed on the internet or the dark web, leaked credentials, code leaks, or exposed sensitive data (Figure 5)
- VIP Protection: Monitoring and blocking of fake accounts for C-level executives, digital appearance analysis, and monitoring of compromised data.
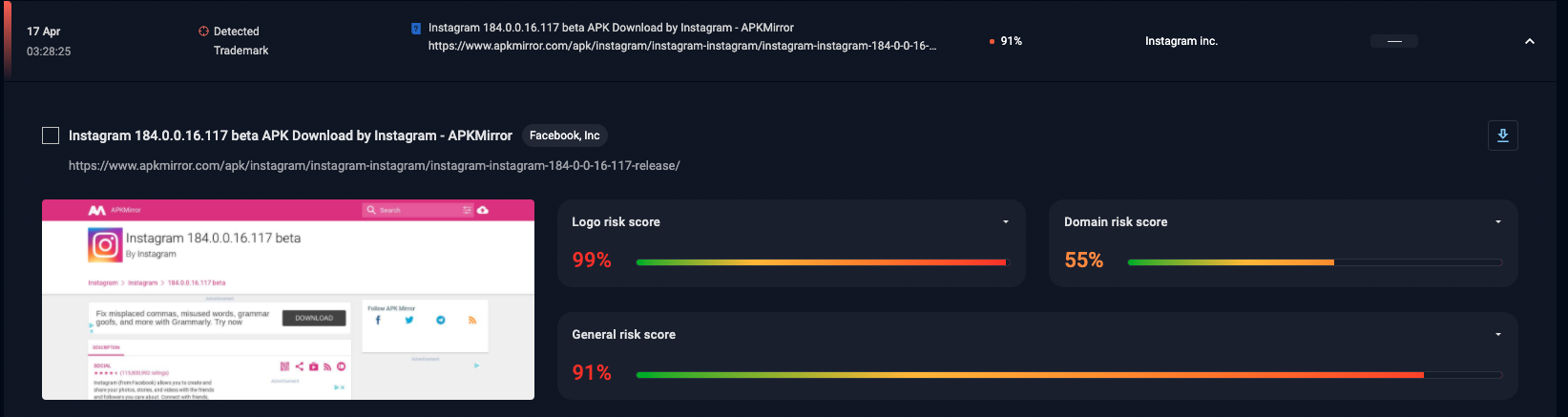
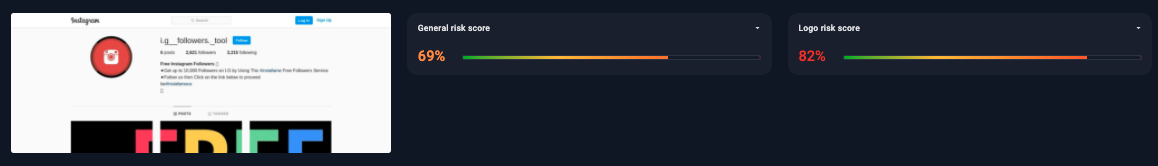
Figure 3 – Suspicious mobile application (Instagram for Android) found on a non-official store. The high general risk score suggests that an action from the brand owner is needed
Group-IB DRP can detect brand mentions in domain names and text content, but it can also detect images misusing logos. The average (general) risk score of the organization’s brand is derived from all analyzed resources. More than 90% of cases of brand violation are automatically detected with machine learning algorithms, which also calculate the general risk score and detect unusual scammer behaviors and patterns. Besides serving as notifications about violations, the risk scores contribute to alert prioritization and are regularly rechecked and updated.
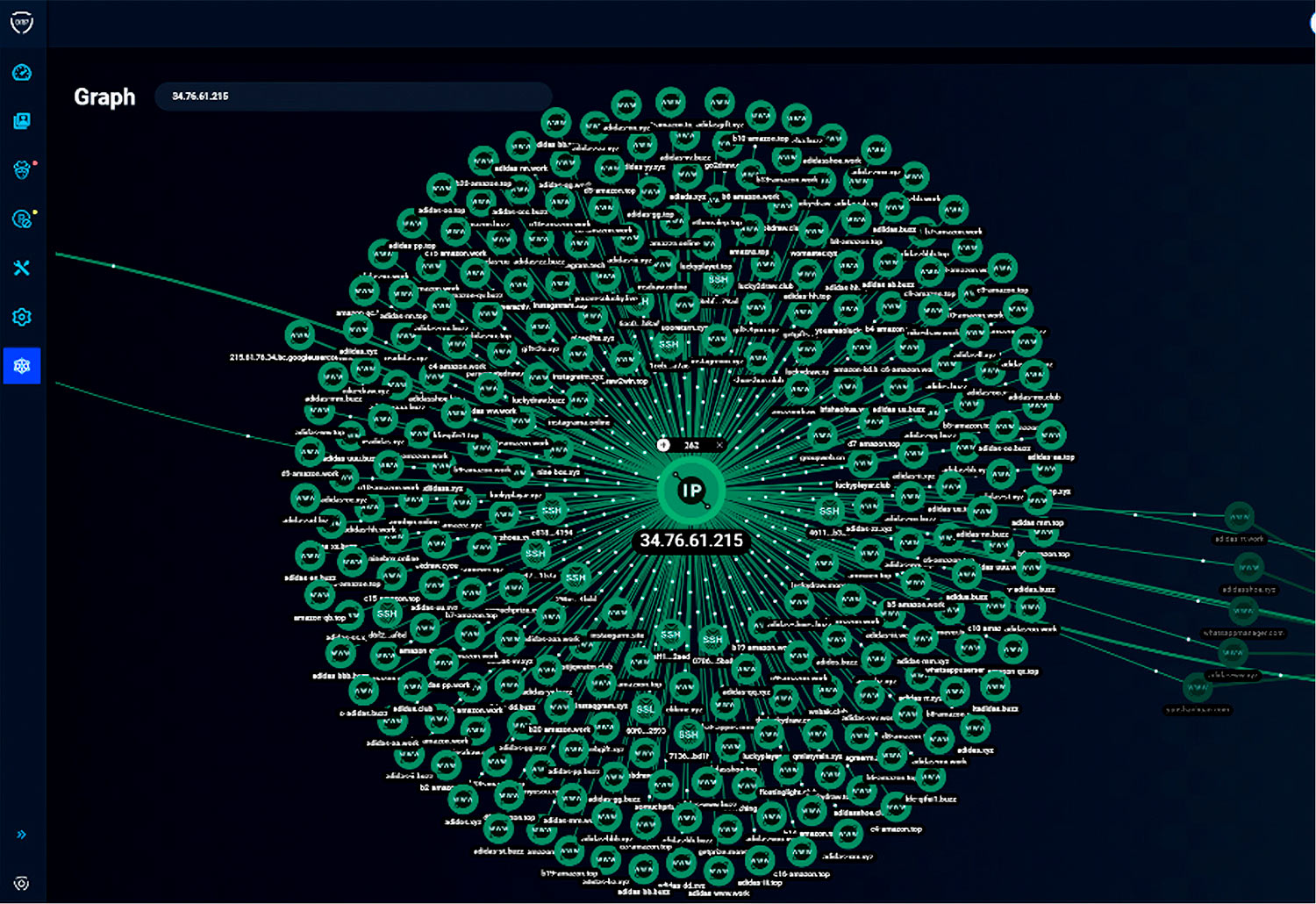
The Group-IB ecosystem enables the enrichment of collected data with existing threat intelligence, a better dissection of criminals’ network infrastructure, and correlation between various campaigns and gangs that are using similar resources. As in other Group-IB products like the Threat Hunting Framework and the Fraud Hunting Platform, users can investigate domains and other artifacts with a practical Graph network analysis that helps organizations grasp the whole picture and the interconnections between gangs and campaigns (Figure 6).
Figures 4 and 5 – Examples of counterfeit and leak detection
If your organization uses a mobile application for its services or customer support Group-IB DRP enables the monitoring of potential misuses like copying and distribution of fake mobile apps on nonstandard marketplaces but also to track new releases on official stores like Google Play and Apple Store. An example of a detected fake mobile application is shown on Figure 3.

Figure 6 – Graph network analysis uncovers the scammers’ infrastructure behind a detected fake Instagram-related domain
Using AI to combat crime and scammers
Human monitoring and manual blocking is not enough to beat back today’s numerous and ever-changing scams. It’s obvious that a lot of effort has gone into making Group-IB DRP powerful at automatic detection and, in general, good at protecting organizations’ digital reputation.
General Risk Scoring enables users to see (and address) the most significant alerts first. The technologies behind the scenes are based on state-of-the-art AI algorithms and deep learning methods, which achieve high accuracy on image recognition and text processing tasks and are cleverly applied on scam-related domain problems.
Risk scores are calculated by AI algorithms that efficiently and continuously learn specifics about the company, as well as context. This is a huge game-changer because this automation enables organizations of all sizes to be equally efficient at spotting real threats.
The processes Group-IB DRP goes through can be grouped in three stages:
- Source monitoring consists of data collection from partner data feeds, crawlers, and private and public APIs
- Data analysis. AI algorithms detect brand misuse in images and text (as well as spot fake claims in images containing text)
- Violation detection. Potential threats, their type and priority, are categorized based on the general, trademark and domain risk scores. After the threat is detected and actions have been made to neutralize it, Group-IB DRP continues to perform regular checks to see if these actions provided results and if the threat is still active. Group-IB DRP uses its reputational database to enrich data, i.e., detected attacker assets (IP address, TLS certificates, names, etc.) are used to build context around the attacker. This component combines the use of classification algorithms and analyst expertise to quickly triage and solve cases of brand misuse
Three main classification technologies calculate the potential risk to the brand:
- The first classification algorithm is used to detect and calculate the domain risk score (Figure 7)
- The second technology detects misuse from the text content, which can be directly extracted from the web page or extracted from images or screenshots of the site. Group-IB DRP works with multiple languages and can understand and classify 95% of the languages used worldwide
- The third technology performs object detection on images and screenshots. The detected object can be the brand logo or another element of the brand’s visual identity that is often misused by scammers (Figure 8)

Figure 7 – The domain risk score is calculated based on various features
Text analysis and object detection contribute to the trademark risk score, which tells us how much the brand is affected by the detected events. All classification technologies take part and contribute to the final general risk score.
Besides the advanced detection mechanisms, Group-IB DRP provides another efficient tool for fast response: users can define signatures (regexes) for fake web pages, so that when the solution encounters a match it can block the resources and contribute additionally to the general risk score.
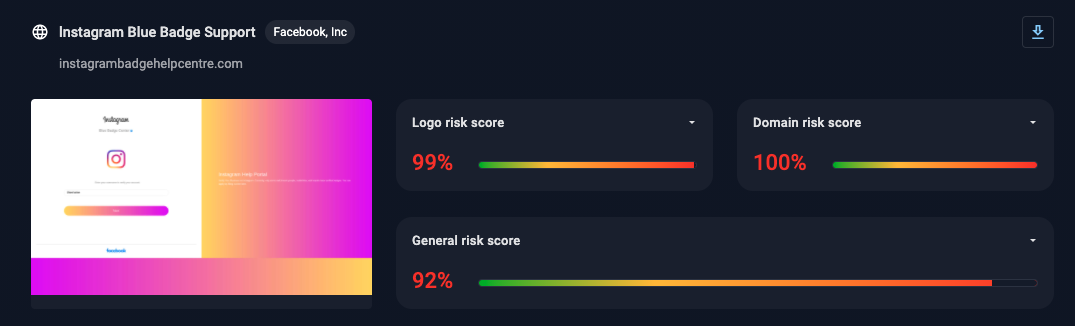
Figure 8 – Detected: Misuse of the Instagram trademark and a high-risk domain
Solving incidents and enforcing actions in the wild
The most interesting part of Group-IB Digital Risk Protection is how the platform leverages the company’s capabilities and expertise to help organizations fight crime.
Besides their own in-house experts, Group-IB can call upon a broad network of partners that includes incident response and law enforcement organizations (national CERTs, IR teams in bigger organizations, ICAAN, etc.). The company’s Computer Emergency Response Team (CERT-GIB) specializes in supporting their clients when it comes to resolving incidents, providing contacts, and establishing communication with significant stakeholders.
Group-IB’s team of analysts is available 24/7/365 and scattered worldwide, which enables them to know specific details and techniques common to the regions that they are monitoring. This in-depth technical knowledge and efficient incident response workflow can help organizations start building their anti-fraud and anti-scam organizational defense, their proactive capabilities, and help mature internal teams improve their capabilities.
Group-IB has established a three-phase process to protect the digital footprint of their clients:
- Notification – In the first phase based on monitoring of collected data, they spot misuses and try to identify the resource owner, establish communication with them and remove the violation. This is usually done in collaboration with domain registrars, hosting providers, associations like CERTs and ICAAN, shared services, or owners of infrastructure that may unknowingly host various malicious content
- Escalation – For specific use cases, Group-IB experts use their partnerships with content delivery platforms to remove violations
- Cease and desists – When the previous steps are unsuccessful, Group-IB experts and their lawyers help the client obtain a pre-trial order to take down the detected violation or, depending on the seriousness of the case, assist the client with alternative next steps
Figures 9 and 10 – Detected suspicious Instagram profile based on trademark misuse
Through this three-phase process, Group-IB DRP enables organizations to reduce digital risks by promptly removing the online brand infringements without the need for additional investment or lengthy litigation. When a fast removal or blocking of all problematic content can’t be achieved quickly, Group-IB DRP moves to minimize the attack and risk surface by adding indicators of compromise to popular phishing databases and blacklists, removing search engine results related to the violation, or blocking social media accounts related to the case.
Real-world case study: The WHO scam
Group-IB DRP was used to detect and take down a scam campaign impersonating the World Health Organization (WHO) in April 2021.
Group-IB Digital Risk Protection was able to detect misuse of the WHO brand, but also to uncover a massive multi-stage scam campaign that consisted of 134 rogue websites impersonating the WHO and encouraging users to take a fake survey.
The scam and related domains were successfully removed through a collaboration between Group-IB and the United Nations International Computing Centre. The scam was simple and went viral because the scammers promised 200 Euro to everyone who completed the survey (which asked for personal data). The victims could also see fake Facebook comments about the gifts the commentators supposedly received. Once users answered the questions, they were prompted to share the link with their WhatsApp contacts to ensure that their multistage scheme was widely distributed.
Using Graph network analysis capabilities Group-IB found that behind the WHO scam campaign was an organized collective dubbed as DarkPath Scammers. Within 48 hours after the first discovery, Group-IB was able to block all rogue domains. Further analysis showed that the domains were connected to 500 other scam and phishing resources impersonating more than 50 well-known international food, sportswear, e-commerce, software, automotive, and energy industry brands. The rogue websites were built with scam kits, which allow scammers to impersonate multiple brands using the same template. After the takedown efforts by the UNICC and Group-IB, the scammers stopped using WHO branding across their entire network.
Figure 11 – The DarkPath collective used 134 domains in the scam campaign related to World Health Day
Conclusion
Group-IB Digital Risk Protection is an innovative product. It helps organizations proactively detect fake domains, fraudulent advertising, and phishing pages. It covers websites, marketplaces, advertising, mobile applications stores, and social media (including Instagram, Twitter, and Facebook).
Due to low technical requirements and the availability of platforms through which customers can be scammed, we will likely soon witness a proliferation of these attacks.
Because the threat actors and tactics they battle against are so different, digital reputation defense solutions differ considerably from classic threat intelligence products. Group-IB has built a rock-solid and specialized product that is supported by their incident response capabilities and is evolving along with the newest attackers’ tactics.
Group-IB DRP can be of help to both big enterprises that own many famous brands and smaller companies that are exposed online and don’t have time and enough personnel to tackle serious cases of misuse of their digital footprint.
As the number of scam campaigns will grow, Group-IB DRP’s Graph network analysis capabilities will be essential. You will want to find the patterns and eliminate the root cause of fraud schemes, and without context this will be impossible.
Scam intelligence is the next frontier due to the increased use of direct communication channels, which allow for better correlation of attackers’ assets and campaigns. The use of AI technologies and the availability of custom tuning to specific regions and customers will enable companies to detect misuses that often fly under the radar of stressed analysts. DRP is equipped with automatization workflows and clever algorithms that save time to security and risk departments while uncovering cases that should be urgently addressed.
We can recommend Group-IB DRP to organizations that wish to protect their brand(s) and are aware of misuse cases of their digital footprint. The verdict is based on the value and scam information that we found during the review.